GitHub Malware Protection Uncovering the Supply Chain Crisis and Amadey Threat
GitHub has become the epicenter of a cybersecurity crisis that demands immediate attention from IT professionals and business leaders. With 39 million secret leaks detected in 2024 alone and sophisticated malware campaigns like Amadey targeting repositories as legitimate hosting platforms, organizations face unprecedented supply chain risks that can cascade across entire ecosystems. This comprehensive analysis reveals that GitHub-based attacks have evolved from simple credential theft to complex multi-stage operations capable of compromising thousands of repositories simultaneously, fundamentally changing how organizations must approach repository security.
The stakes have never been higher. Recent attacks demonstrate that GitHub’s corporate legitimacy and widespread access make it an ideal vector for bypassing traditional security filters, while the interconnected nature of modern software development creates cascading vulnerabilities where a single compromised component can affect thousands of downstream projects. Organizations must now treat GitHub security not as a developer convenience but as a critical infrastructure protection requirement.
Table of Contents
Amadey malware campaign exposes GitHub’s vulnerability to sophisticated attacks
The April 2025 Amadey malware campaign represents a watershed moment in GitHub-based threats, demonstrating how attackers have weaponized the platform’s trust and accessibility. Cisco Talos Intelligence identified three compromised GitHub accounts hosting 160+ repositories, each containing single malicious files designed to bypass corporate web filters. The campaign leveraged GitHub’s corporate reputation to deliver a sophisticated malware-as-a-service operation, with the primary account “Legendary99999” serving as a distribution hub for multiple malware families including Lumma Stealer, RedLine Stealer, and AsyncRAT.
The attack methodology reveals concerning sophistication levels. Attackers embedded PowerShell commands within Python scripts masquerading as cryptocurrency tools, with hardcoded IP addresses for payload retrieval and error messages in broken Cyrillic suggesting Russian-speaking threat actors. The campaign’s success stemmed from exploiting GitHub’s legitimate appearance corporate networks that would normally block suspicious domains readily accessed malware hosted on github.com repositories.
This represents a tactical evolution in cybercrime, where attackers have moved beyond traditional hosting to abuse trusted platforms. The Amadey campaign generated substantial financial impact through credential theft and cryptocurrency hijacking, while demonstrating how GitHub’s collaborative features can be weaponized for malware distribution at scale.
Attack vectors exploit GitHub’s collaborative architecture
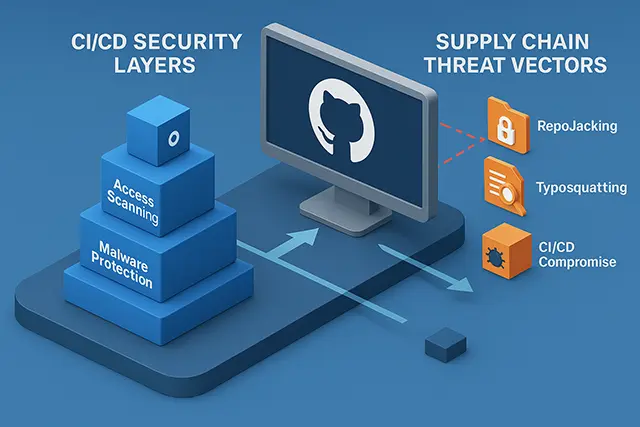
GitHub’s fundamental design creates multiple attack surfaces that cybercriminals increasingly exploit with devastating effectiveness. Repository hijacking affects 9 million repositories according to AquaSec research, with 2.95% of analyzed repositories potentially vulnerable to “RepoJacking” attacks where organizations rebrand or rename repositories without proper redirect management. Attackers exploit this by creating repositories with former names, capturing traffic from dependent projects.
The tj-actions/changed-files compromise exemplifies supply chain attack sophistication. Attackers began with a vulnerable pull_request_target trigger in the SpotBugs repository, escalated to compromise reviewdog/action-setup through stolen personal access tokens, and ultimately poisoned the tj-actions/changed-files action affecting 23,000+ repositories. The attack utilized “shadow commits” from deleted forks and overridden Git tags to maintain persistence while evading detection.
Typosquatting represents another critical vector, with researchers successfully creating 14 typosquatted GitHub Actions organizations that attracted 194 workflow references within two months. Common patterns include “actons” versus “actions” and “circelci” versus “circleci,” demonstrating how simple spelling errors can lead to malicious code execution in CI/CD pipelines.
Technical vulnerabilities compound these risks. Recent Git CVEs include CVE-2024-32002 with a CVSS score of 9.1, enabling remote code execution through submodule manipulation where attackers craft repositories that exploit Git’s file writing behavior to execute hooks during clone operations. GitHub Enterprise Server faces additional risks through CVE-2024-6800, allowing unauthenticated attackers to forge SAML responses and gain administrative access.
Security tools landscape spans free solutions to enterprise platforms
GitHub’s native security ecosystem provides comprehensive protection through GitHub Advanced Security (GHAS), which detected and prevented millions of secret exposures in 2024. The platform achieved a 75% precision rate in secret detection, significantly outperforming alternatives, while scanning 1.1 billion commits for credential exposure. GitHub Secret Protection ($19/month per active committer) provides real-time detection of 350+ secret types with push protection capabilities, while GitHub Code Security ($30/month per active committer) offers CodeQL-powered vulnerability scanning with AI-generated remediation suggestions.
Free solutions include GitHub’s basic secret scanning for public repositories, Dependabot for dependency vulnerability management, and CodeQL for static application security testing. The platform’s SARIF support enables integration with third-party tools like Snyk, Checkmarx, and Trivy, creating comprehensive security scanning workflows.
Enterprise-grade solutions extend beyond GitHub’s native offerings. Snyk provides comprehensive SAST, SCA, and container scanning with native GitHub integration, while Checkmarx offers enterprise-grade security testing capabilities. Open source alternatives include Trivy for container vulnerability scanning, SonarQube for code quality and security analysis, and Semgrep for custom rule-based static analysis. For comprehensive security guidance, the OWASP Top 10 provides essential vulnerability awareness for development teams.
Integration methods vary from GitHub Actions workflow automation to direct platform integration through GitHub Apps. Organizations can implement automated security scanning pipelines that combine multiple tools, upload results through SARIF format, and create unified security dashboards for comprehensive vulnerability management.
Implementation requires a phased approach: foundation security with MFA and branch protection, enhanced security through GHAS deployment, advanced integration with third-party tools, and optimization through configuration tuning and team training. Organizations typically see significant ROI within 3-6 months through reduced security incidents and improved compliance posture.
Enterprise security demands comprehensive governance and automation
Enterprise GitHub security requires sophisticated governance frameworks that balance developer productivity with security requirements. GitHub Enterprise Security features include organization-wide security configuration templates, role-based access control with security manager permissions, and comprehensive audit logging with real-time streaming to enterprise SIEM platforms. The platform supports integration with major SIEM solutions including Splunk, Microsoft Sentinel, and Datadog for centralized security monitoring.
DevSecOps practices have become essential for preventing malicious code injection. Organizations must implement shift-left security approaches that integrate automated scanning into CI/CD pipelines, pre-commit hooks for security validation, and continuous security testing throughout the software development lifecycle. GitHub Actions security workflows enable SAST integration with tools like Semgrep and Bearer, dynamic application security testing automation, and infrastructure-as-code security validation.
Security automation frameworks provide crucial capabilities for enterprise-scale operations. Automated response capabilities include security alert auto-triage, vulnerability remediation workflows, and incident response automation with SOAR platform integration. Organizations implementing comprehensive automation report 60% faster vulnerability remediation with GitHub Copilot Autofix capabilities.
Access control and role management require sophisticated organizational policies. Security manager roles provide dedicated security alert access and management, security feature enablement capabilities, and compliance reporting support. Enterprise organizations must implement federated identity management integration, multi-factor authentication enforcement, and regular access reviews to maintain security posture.
Industry statistics reveal escalating threats with significant business impact
GitHub-based attacks have reached alarming frequency with substantial business consequences. The 39 million secret leaks detected in 2024 represent a 30.3% increase from the previous year, with 58% consisting of generic secrets that are most challenging to validate and remediate. Private repositories demonstrate 8x higher likelihood of containing secrets compared to public repositories, while 3.11% of secrets leaked in private repositories were also exposed in public repositories.
Financial impact extends far beyond direct theft. The global cybersecurity market reached $354.7 billion in 2024 with projections to reach $502.1 billion by 2029, driven largely by supply chain security concerns. 67% of organizations delayed application deployment due to security concerns, while 26% reported employee termination and 30% faced fines following security incidents. The GitVenom campaign alone resulted in $485,000 in Bitcoin theft, demonstrating the direct financial consequences of GitHub-based attacks. According to NIST’s National Vulnerability Database, GitHub-related vulnerabilities have increased significantly, requiring organizations to prioritize repository security as a critical component of their cybersecurity strategy.
Industry distribution reveals that IT sector accounts for 65.9% of all detected leaks, followed by education (20.1%), science and technology (7%), and manufacturing (1.2%). The banking, financial services, and insurance sector holds 25% market share in cybersecurity investments, reflecting the critical importance of repository security in highly regulated industries.
Expert opinions emphasize the criticality of GitHub security investments. As Eric Fourrier, CEO of GitGuardian, warns: “Developers erasing leaky commits or repositories instead of revoking are creating a major security risk for companies, which will remain vulnerable to threat actors mirroring public GitHub activity for as long as the credential remains valid.” Industry analysis consistently identifies GitHub as ground zero for supply chain attacks, requiring priority investment attention.
Emerging trends shape the future of repository security
The GitHub security landscape continues evolving with AI-powered attack sophistication and defense mechanisms. Threat actors increasingly leverage AI tools for code analysis and attack automation, while defenders deploy AI-powered security solutions like GitHub Copilot Autofix for automated vulnerability remediation. The platform processed 10.54 billion GitHub Actions minutes in 2024, representing a 30% increase year-over-year and expanding the attack surface for CI/CD compromise.
Supply chain attacks have become the primary vector for large-scale compromises, with attackers exploiting GitHub’s collaborative features to introduce malicious code through sophisticated fork-based attacks. The expansion of secrets sprawl beyond code repositories to package managers like PyPI and npm creates additional attack vectors that organizations must address through comprehensive security strategies.
Technology evolution demonstrates both increasing threats and improving defenses. GitHub serves as the 5th largest CVE Numbering Authority with 2,000+ CVE records published in 2024, while the GitHub Advisory Database contains 20,000+ reviewed advisories compared to 400 five years ago. Secret scanning precision improvements have reduced false positives significantly, while push protection capabilities have blocked millions of secrets before exposure.
Platform growth continues with 100+ million developers and 420+ million repositories hosting critical infrastructure code. GitHub Copilot adoption reached 1.3 million paying subscribers, while the platform’s role in enterprise development workflows continues expanding. Organizations must adapt their security strategies to address this growing attack surface while maintaining developer productivity.
Best Practices for GitHub Malware Protection
To effectively counter evolving threats on GitHub, organizations must implement a layered security approach that combines prevention, detection, and response. These best practices help reduce risk across both public and private repositories, CI/CD pipelines, and third-party dependencies.
- Enable Secret Scanning and Push Protection: Use GitHub’s native features or third-party tools to detect exposed credentials and prevent them from being committed in the first place.
- Implement Branch Protection Rules: Enforce pull request reviews, signed commits, and status checks before allowing code to merge into protected branches.
- Use GitHub Advanced Security (GHAS): Leverage CodeQL and Dependabot to catch vulnerabilities early and automate remediation across your codebase.
- Conduct Regular Repo Audits: Review contributors, permissions, and repo settings to minimize unnecessary access and privilege escalation risks.
- Validate GitHub Actions Sources: Avoid referencing third-party actions without validating source code, SHA hashes, or using verified publishers.
- Monitor for RepoJacking and Typosquatting: Claim legacy repository names, monitor workflow references, and use security monitoring tools to detect suspicious forks or impersonations.
- Harden CI/CD Pipelines: Disable untrusted inputs in GitHub Actions, isolate jobs with minimal permissions, and enable logging/auditing on build systems.
- Train Developers on Secure Git Practices: Educate your teams about the risks of exposed tokens, malicious dependencies, and insecure workflows. Awareness reduces human error.
By applying these practices consistently, organizations can significantly reduce their exposure to GitHub-based threats and establish a stronger security baseline across development environments.
Recommendations for immediate action and long-term security posture
Organizations must implement immediate protective measures while building comprehensive long-term security strategies. Enable push protection to prevent secret exposure before commits, conduct organization-wide secret risk assessments, and rotate exposed credentials following discovery. Deploy comprehensive audit logging for all repository activities and establish security alert management processes for rapid incident response.
Strategic initiatives should focus on DevSecOps integration and automated security scanning. Implement automated security testing workflows with AI-powered remediation capabilities, establish supply chain security governance for third-party dependencies, and invest in security awareness training for development teams. Organizations should prioritize GitHub security as fundamental infrastructure protection rather than optional developer tooling.
Long-term security posture requires zero-trust architecture implementation for all repository access and permissions. Deploy continuous monitoring with threat intelligence integration, conduct regular security assessments including penetration testing, and develop incident response plans specifically for repository compromise scenarios. The business case for GitHub security investment remains compelling: prevention costs significantly outweigh potential attack impact, particularly given supply chain implications affecting entire organizational ecosystems.
Conclusion
The GitHub security landscape in 2025 demands immediate organizational attention and substantial investment. With sophisticated campaigns like Amadey demonstrating how attackers weaponize platform trust, organizations face unprecedented supply chain risks that traditional security measures cannot address. The combination of 39 million secret leaks, complex multi-stage attacks, and growing financial impact creates a cybersecurity crisis requiring comprehensive response strategies.
Success depends on implementing multi-layered security approaches that combine GitHub’s native security tools with third-party solutions and robust governance practices. Organizations must treat GitHub security as critical infrastructure protection, implementing automated scanning, continuous monitoring, and comprehensive incident response capabilities. The interconnected nature of modern software development means that repository security failures can cascade across entire ecosystems, making prevention not just organizationally critical but industrially essential.
The path forward requires immediate action on fundamental security measures while building toward comprehensive DevSecOps integration and automated threat response. Organizations that act decisively now will establish competitive advantages through secure development practices, while those that delay face escalating risks in an increasingly hostile threat landscape. The GitHub security crisis represents both a critical challenge and an opportunity for organizations to fundamentally strengthen their cybersecurity posture through proactive, comprehensive security strategies.