Latest in NCSE Blog
Stay informed with insights, updates, and breakthroughs shaping the future.

7 Essential Tips for Choosing the Right Store When Buying Premium Smartphones Like Samsung S25 Zahir Fahmi

AI in Daily Life: The Invisible Revolution Happening Right Under Your Nose Zahir Fahmi

What’s an eSIM Card and Should You Use It For Business?
In an increasingly digital and mobile-driven business landscape, staying connected seamlessly across teams, locations, and time zones is essential. Enter the eSIM card, a modern solution transforming how companies manage…
Zahir FahmiEditor’s Picks
Top editorial highlights

Minecraft Server Hosting That Actually Works: What Most Gamers Overlook Zahir Fahmi

How Artificial Intelligence Is Redefining the Jewelry Experience: From Bench… Zahir Fahmi

SaaS Onboarding Platform: Why 73% of Users Quit Before Experiencing… Zahir Fahmi

Post-Quantum Cryptography: The Technical Guide to Securing Your Infrastructure Against… Zahir Fahmi
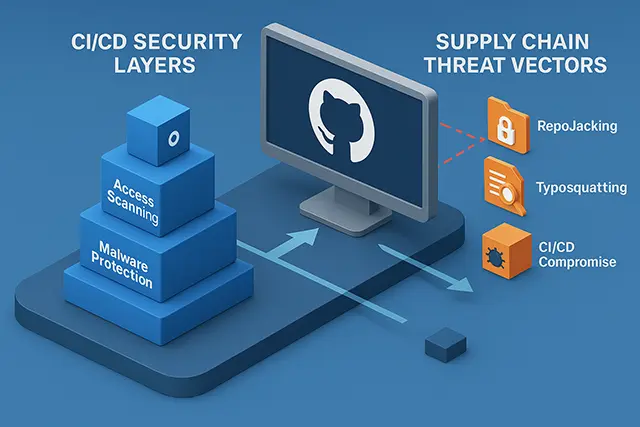
GitHub has become the epicenter of a cybersecurity crisis that demands immediate attention from
18 July 2025
The cloud misconfiguration that exposed our entire customer database was a simple S3 bucket
15 July 2025
Last Tuesday, I watched a senior IT director stare at her screen for thirty
13 July 2025
Note: This article provides an informational overview based on publicly available information. Cryptocurrency and
09 July 2025
During what started as a routine threat hunting exercise, our security team uncovered anomalies
09 July 2025
The most damaging insider threat attacks I've investigated turned out to be a trusted
06 July 2025
Remember when you found that perfect video on X but couldn't figure out how
03 July 2025
The boardroom presentation that finally got zero trust approved was surprisingly simple: I showed
03 July 2025
Let me walk you through what happens when SQL meets carelessness and how to
01 July 2025