The Quantum Threat Timeline: When Your Encryption Expires

You wake up one morning to find that every encrypted file in your company every customer record, every financial transaction, every piece of intellectual property is suddenly as readable as a billboard on Times Square. This isn’t science fiction. It’s the looming reality of quantum threats that keeps CISOs awake at night. As organizations begin to understand post-quantum cryptography, the urgency of addressing these vulnerabilities becomes increasingly clear.
The quantum computing revolution promises incredible breakthroughs in medicine, materials science, and artificial intelligence. But there’s a darker side to this technological leap forward that most businesses aren’t prepared for. The same quantum computers that could cure cancer might also crack the encryption protecting your most sensitive data in minutes rather than millennia.
Table of Contents
The Real Deal About Quantum Threats
I’ve sat through dozens of vendor pitches about quantum threats, and honestly? Most of them sound like bad sci-fi movies. But strip away the hype, and you’re left with a simple, terrifying truth: the math that protects literally everything digital is about to become obsolete.
Here’s the thing that clicked for me: We’ve built our entire digital world on one assumption that certain math problems are too hard for computers to solve quickly. Banking apps, WhatsApp messages, VPN connections, even your smart doorbell they all depend on this mathematical difficulty.
Quantum computers don’t play by those rules. Where a regular computer tries every possible solution one by one like checking every possible combination on a giant safe, quantum computers can try multiple solutions simultaneously. It’s not magic it’s physics. And it’s coming whether we’re ready or not.
Breaking Down the Timeline Without the BS
Everyone wants to know “when?” Fair question. The honest answer? Nobody knows exactly, but the smart money says we’ve got about 10-15 years before quantum computers can reliably crack current encryption. Some experts think sooner, some think later.
But here’s what most articles miss: The timeline doesn’t actually matter as much as you think.
Why? Because of something security folks call “harvest now, decrypt later.” Imagine someone photocopying your locked diary today, planning to read it when they invent a way to decode your handwriting. That’s essentially what nation-states and sophisticated hackers are doing right now with encrypted data.
The Y2Q Timeline: When Encryption Expires
Unlike Y2K, which had a fixed deadline, the quantum threat operates on a sliding scale of probability. Security experts call this Y2Q the year when quantum computers become powerful enough to break current encryption standards. But here’s the kicker: the threat isn’t just about when quantum computers become powerful enough; it’s also about “harvest now, decrypt later” attacks happening today.
2025-2030: The Preparation Phase
We’re currently in what experts call the “preparation window.” Quantum computers with 100-1000 logical qubits are emerging, but they’re still too error-prone and limited to pose an immediate threat to encryption. However, this is precisely when organizations need to act. It’s like knowing a hurricane is forming in the Atlantic you don’t wait until it makes landfall to board up the windows.
During this phase, quantum computing and cyber security intersect in fascinating ways. Organizations are beginning to inventory their cryptographic assets, identifying which systems are most vulnerable and prioritizing them for upgrades. Smart companies are already implementing crypto-agility the ability to quickly swap out encryption methods when needed.
The financial sector provides an illuminating example. Major banks are already running quantum risk assessments, not because they expect quantum computers to crack their encryption tomorrow, but because they understand the long tail of cryptographic vulnerability. A mortgage document encrypted today might still need protection 30 years from now.
2030-2035: The Critical Transition
This is when things get serious. Quantum computers with 1,000-10,000 logical qubits will likely emerge, bringing us dangerously close to the cryptographic breaking point. The quantum computing threat to cybersecurity transforms from theoretical to practical during this window.
Consider what happened with SHA-1 encryption. Security researchers warned for years that it was becoming vulnerable, but many organizations dragged their feet on migration. When Google finally demonstrated a practical collision attack in 2017, the scramble to upgrade was chaotic and expensive. The quantum transition will be similar but on a massive scale.
2035 and Beyond: The Quantum Era
By this point, quantum computers powerful enough to break current encryption will likely exist. Organizations still using pre-quantum cryptography will be as vulnerable as those using passwords like “123456” today. The landscape of cyber security in quantum computing will be fundamentally different, with quantum-safe algorithms being the minimum standard rather than cutting-edge technology.

The “Harvest Now, Decrypt Later” Threat
Here’s something that should make every executive nervous: the quantum threat isn’t just about future vulnerabilities. Nation-states and sophisticated threat actors are already stealing encrypted data today, betting they’ll be able to decrypt it once quantum computers become available. It’s like someone photographing your locked safe, knowing they’ll eventually have a tool to open it.
This creates an interesting paradox. Data encrypted today using current standards might have a cryptographic expiration date of 2035, but if that data needs protection beyond that point, it’s already compromised. Financial records, medical data, trade secrets, and government communications fall into this category.
The U.S. government takes this seriously enough that the NSA has been urging organizations to transition to quantum-resistant cryptography since 2015. They’re not worried about quantum computers appearing tomorrow they’re worried about protecting information that needs to remain secret for decades. NIST’s recent finalization of post-quantum standards in August 2024 marks a critical milestone in this transition.
Real-World Quantum Computing Security Risks
Let’s move beyond theory and examine specific quantum computing security risks that organizations face today. These aren’t hypothetical scenarios but real vulnerabilities that security teams need to address.
Table 1: Quantum Threat Timeline and Impact Assessment
| Time Period | Quantum Capability | Vulnerable Systems | Business Impact | Required Action |
|---|---|---|---|---|
| 2025-2027 | 100-1,000 logical qubits | Legacy cryptographic systems | Low-Medium | Begin assessment and planning |
| 2028-2030 | 1,000-10,000 logical qubits | RSA-2048, ECC-256 | Medium-High | Active migration to PQC |
| 2031-2035 | 10,000+ logical qubits | Most current encryption | Critical | Complete PQC implementation |
| 2035+ | Fault-tolerant QC | All classical cryptography | Catastrophic | Quantum-safe by default |
Public Key Infrastructure Collapse
The entire internet runs on public key cryptography. Every time you see that padlock icon in your browser, you’re relying on RSA or elliptic curve cryptography to protect your data. Quantum computers running Shor’s algorithm could break these systems entirely, essentially eliminating secure communication as we know it.
Imagine trying to run an e-commerce business when credit card transactions can’t be encrypted securely. Or consider healthcare providers unable to protect patient data during transmission. The ripple effects would be catastrophic.
Blockchain and Cryptocurrency Vulnerabilities
Cryptocurrencies rely heavily on cryptographic signatures that quantum computers could forge. The quantum computing threat to cryptography extends directly to the $2 trillion cryptocurrency market. Bitcoin addresses, Ethereum smart contracts, and other blockchain-based systems all face existential threats from quantum computing.
This isn’t just about losing digital money. Many organizations are building critical infrastructure on blockchain technology, from supply chain management to digital identity systems. All of these implementations need quantum-resistant upgrades.
Long-Term Data Protection Failures
Some data needs protection for decades. Medical records, government classified information, and corporate trade secrets fall into this category. Organizations encrypting this data today using classical methods are essentially putting an expiration date on its confidentiality.
Consider pharmaceutical companies protecting drug formulas or defense contractors safeguarding weapons designs. If this information is stolen today in encrypted form, it might be readable in 10-15 years when quantum computers mature. The competitive and security implications are staggering.
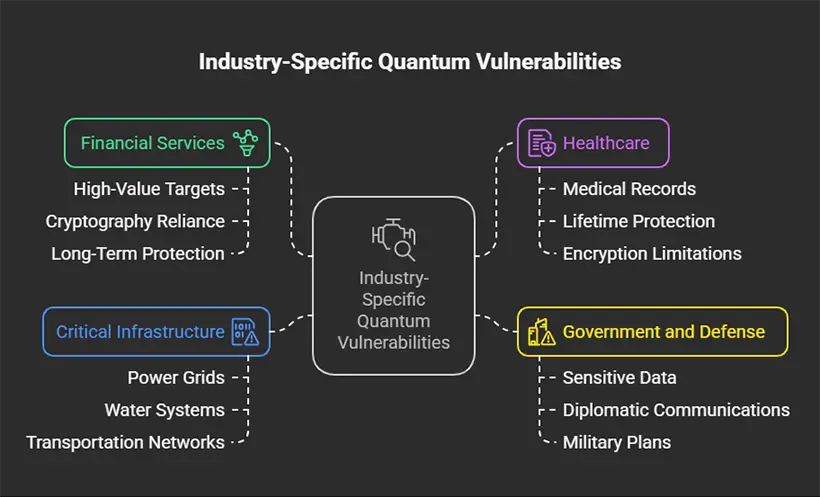
Industry-Specific Quantum Vulnerabilities
Different sectors face unique challenges when it comes to quantum threats. Understanding these industry-specific vulnerabilities helps organizations prioritize their quantum security efforts.
Financial Services: The Prime Target
Banks and financial institutions are particularly vulnerable to quantum threats for several reasons. First, they’re high-value targets with massive amounts of sensitive data. Second, they rely heavily on cryptography for everything from ATM transactions to international wire transfers. Third, financial data often needs long-term protection due to regulatory requirements.
The quantum cyber risk in banking extends beyond direct attacks. Consider the interconnected nature of global finance. If one major bank’s cryptographic systems fail, it could trigger a cascade of failures across the entire financial system. This systemic risk keeps central bankers awake at night.
Major financial institutions are already taking action. JPMorgan Chase, for instance, has been researching quantum-resistant blockchain technologies. Barclays and IBM have partnered to explore quantum-safe cryptography implementations, as detailed in IBM’s quantum network initiatives. These aren’t research projects hidden in labs they’re strategic initiatives with real budgets and timelines.
Healthcare: Life-and-Death Encryption
Healthcare organizations face unique challenges with quantum threats. Medical records need protection for a patient’s entire lifetime potentially 100 years or more. Current encryption methods simply can’t guarantee that level of long-term security against quantum attacks.
The stakes go beyond privacy. Consider connected medical devices like pacemakers or insulin pumps. If quantum computers could break the encryption protecting these devices, hackers could potentially harm or kill patients remotely. It sounds like a movie plot, but it’s a real concern driving quantum security research in healthcare.
Government and Defense: National Security at Risk
Government agencies hold some of the most sensitive data on the planet. Diplomatic communications, military plans, intelligence gathering all rely on encryption that quantum computers could eventually break. The quantum computing security threat to national security is so significant that it’s driving billions in research funding.
The U.S. Department of Defense has identified quantum computing as one of the critical technologies for maintaining military superiority. They’re not just worried about protecting current communications but also about the vast archives of classified information that could become readable in the quantum era.
Critical Infrastructure: The Hidden Vulnerability
Power grids, water systems, transportation networks our critical infrastructure increasingly relies on encrypted communications for safe operation. The cyber security and quantum computing intersection becomes particularly dangerous here because these systems often use older, harder-to-upgrade technology.
Imagine a scenario where quantum computers could break the encryption protecting power grid control systems. Bad actors could potentially cause widespread blackouts, endangering lives and causing billions in economic damage. This isn’t fear-mongering it’s a scenario that infrastructure security experts actively plan against.
The Quantum Defense Playbook
Understanding the threat is only half the battle. Organizations need concrete steps to protect themselves against quantum attacks. Here’s what forward-thinking companies are doing today to prepare for tomorrow’s quantum reality.
Cryptographic Asset Inventory
You can’t protect what you don’t know about. The first step in quantum defense is creating a comprehensive inventory of all cryptographic implementations across your organization. This includes:
- Encryption algorithms used in databases
- Communication protocols for internal and external connections
- Digital signature systems for document integrity
- Key management infrastructure
- Third-party services and their encryption methods
This inventory process often reveals surprising vulnerabilities. Many organizations discover they’re using deprecated encryption methods they thought were retired years ago. Legacy systems, in particular, often harbor cryptographic time bombs.
Implementing Crypto-Agility
Crypto-agility is the ability to quickly swap out cryptographic algorithms when they become vulnerable. Think of it like having modular components in your security architecture that can be replaced without rebuilding the entire system. This concept becomes even more critical as you explore advanced post-quantum cryptography strategies.
Table 2: Crypto-Agility Implementation Framework
| Component | Current State | Transition State | Quantum-Safe State | Timeline |
|---|---|---|---|---|
| TLS/SSL | RSA-2048, ECDSA | Hybrid RSA+Kyber | ML-KEM only | 2025-2027 |
| VPN | IPsec with AES | Hybrid classical+PQC | Full PQC protocols | 2026-2028 |
| Code Signing | RSA/ECDSA | Dual signatures | ML-DSA/SLH-DSA | 2025-2027 |
| Email Security | S/MIME RSA | Hybrid approach | PQC signatures | 2026-2028 |
| Database Encryption | AES-256 | No change needed | Enhanced key management | Ongoing |
This requires fundamental changes to how organizations design systems. Instead of hard-coding encryption methods, applications need abstraction layers that allow algorithm changes through configuration rather than code modifications. It’s more complex initially but pays dividends when quantum threats materialize.
Hybrid Cryptographic Approaches
Smart organizations aren’t waiting for perfect quantum-resistant algorithms. They’re implementing hybrid approaches that combine classical and post-quantum cryptography. This belt-and-suspenders approach ensures security even if one algorithm fails.
For example, you might encrypt data using both RSA and a lattice-based algorithm. An attacker would need to break both to access the data. This approach adds some overhead but provides insurance during the uncertain transition period.
Quantum Security Testing and Assessment
Regular testing becomes crucial as quantum threats evolve. Organizations need to assess their quantum readiness continuously, not just once. This includes:
- Vulnerability scanning for quantum-weak encryption
- Penetration testing with quantum threat scenarios
- Third-party security assessments focused on quantum risks
- Supply chain analysis for quantum vulnerabilities
The cyber quantum landscape changes rapidly, making continuous assessment essential. What seems quantum-safe today might be vulnerable tomorrow as quantum computers improve.

The Economics of Quantum Defense
Here’s where rubber meets road for most organizations: what does quantum defense cost, and is it worth it? The economics of quantum computing for cyber security create interesting trade-offs that executives need to understand.
The Cost of Action vs. Inaction
Implementing quantum-safe cryptography isn’t free. Organizations face costs including:
- Software upgrades and replacements
- Hardware modifications for better performance
- Training for IT staff
- Potential compatibility issues with partners
- Performance overhead from stronger encryption
However, the cost of inaction could be catastrophic. A single quantum-enabled breach could expose decades of sensitive data, resulting in regulatory fines, lawsuits, competitive disadvantages, and irreparable reputation damage. The equation isn’t whether to invest in quantum defense but how quickly to do so.
ROI Calculations for Quantum Security
Calculating return on investment for quantum security investments requires thinking differently about risk. Traditional security ROI models assume threats exist today. Quantum threats operate on a different timeline, requiring probabilistic models that account for:
- The likelihood of quantum computers reaching cryptographic relevance
- The value of data needing long-term protection
- The cost of breaches at different future points
- The decreasing cost of quantum defenses over time
Forward-thinking CFOs are already building these models, recognizing that early investment in quantum security is like buying insurance before premiums skyrocket.
Budget Allocation Strategies
Organizations can’t upgrade everything at once. Smart budget allocation for quantum defense follows a risk-based approach:
- High-value, long-term data: Prioritize systems protecting data that needs decades of security
- External-facing systems: Focus on internet-exposed services that adversaries can easily target
- Compliance-driven upgrades: Address systems where regulations will eventually mandate quantum security
- Strategic partnerships: Invest in connections with key partners who are also upgrading
This phased approach spreads costs over time while addressing the most critical vulnerabilities first.
Global Quantum Security Initiatives
The quantum threat transcends borders, spurring international cooperation on unprecedented scales. Understanding these global initiatives helps organizations align their quantum security strategies with emerging standards.
NIST Post-Quantum Cryptography Standardization
The U.S. National Institute of Standards and Technology (NIST) has been leading the charge on quantum-resistant cryptography standards since 2016. After evaluating dozens of algorithms, they’ve selected several for standardization. According to NIST’s official announcement, the finalized standards include:
Table 3: NIST Post-Quantum Cryptography Standards (2024)
| Standard | Algorithm Name | Use Case | Key Features | Status |
|---|---|---|---|---|
| FIPS 203 | ML-KEM (formerly CRYSTALS-Kyber) | General encryption | Small keys, fast operation | Finalized Aug 2024 |
| FIPS 204 | ML-DSA (formerly CRYSTALS-Dilithium) | Digital signatures | Lattice-based security | Finalized Aug 2024 |
| FIPS 205 | SLH-DSA (formerly SPHINCS+) | Hash-based signatures | Stateless design | Finalized Aug 2024 |
| Draft FIPS 206 | FN-DSA (formerly FALCON) | Compact signatures | FFT over NTRU | Expected 2025 |
| TBD | HQC | Backup KEM | Error-correcting codes | Selected March 2025 |
These aren’t just academic exercises. Major technology companies are already implementing these algorithms, and they’ll likely become mandatory for government contractors within the next few years. IBM’s Quantum Developer Conference 2024 showcased how these standards are being integrated into real-world systems.
International Cooperation and Competition
While countries cooperate on standards, they’re also competing fiercely in quantum computing development. The U.S., China, and the European Union are pouring billions into quantum research, recognizing its strategic importance.
This creates interesting dynamics for multinational corporations. They need quantum defenses that work across different regulatory regimes while navigating the geopolitical implications of quantum technology. It’s not just about technical standards but also about export controls, data sovereignty, and international partnerships.
Industry-Specific Quantum Guidelines
Various industries are developing their own quantum security guidelines tailored to specific needs:
- Financial services: The Financial Services Information Sharing and Analysis Center (FS-ISAC) provides quantum threat intelligence
- Healthcare: HIPAA compliance will eventually require quantum-safe encryption
- Telecommunications: The GSM Association is working on quantum-safe 5G and 6G standards
- Automotive: Connected car manufacturers are developing quantum-resistant vehicle communication protocols
Organizations need to track both general quantum security developments and industry-specific requirements to stay compliant and secure.
Practical Steps for Immediate Action
While the full impact of quantum threats may be years away, organizations need to act now. Here’s a practical roadmap for immediate action that balances urgency with pragmatism. Organizations that have already begun implementing post-quantum cryptography solutions report significant advantages in preparedness and competitive positioning.
Phase 1: Assessment and Awareness (Next 90 Days)
Start with education and assessment. Many executives and board members don’t fully understand quantum threats. Key actions include:
- Executive briefings: Educate leadership on quantum risks specific to your industry
- Risk assessment: Identify data and systems needing long-term protection
- Vendor analysis: Survey key technology vendors about their quantum roadmaps
- Skill gap analysis: Determine what quantum security expertise you need
This phase is about building organizational awareness and getting buy-in for longer-term investments.
Phase 2: Planning and Piloting (Months 4-12)
With awareness established, move to concrete planning:
- Develop quantum security strategy: Create a multi-year roadmap for quantum defense
- Pilot projects: Test quantum-safe algorithms in non-critical systems
- Partnership development: Connect with quantum security vendors and consultants
- Budget allocation: Secure funding for quantum security initiatives
This phase transforms awareness into action, albeit on a limited scale to learn and refine approaches.
Phase 3: Implementation and Integration (Year 2+)
Full implementation takes time but follows a clear path:
- Systematic upgrades: Roll out quantum-safe cryptography based on risk priorities
- Continuous monitoring: Implement quantum threat intelligence and monitoring
- Partner coordination: Ensure key partners and suppliers are also quantum-ready
- Regular updates: Stay current with evolving quantum threats and defenses
Remember, this isn’t a one-time project but an ongoing evolution of your security posture.
The Role of Quantum Security Vendors
A growing ecosystem of vendors offers quantum security solutions. Understanding this landscape helps organizations choose the right partners for their quantum defense journey.
Pure-Play Quantum Security Companies
Specialized companies focusing exclusively on quantum security offer deep expertise:
- Post-quantum VPN providers: Companies like Quantum Xchange offer quantum-safe communication channels
- Quantum key distribution: Vendors providing physics-based quantum security
- Quantum random number generators: Hardware ensuring truly random encryption keys
- Quantum security assessment: Specialized consultants evaluating quantum readiness
These specialists often provide cutting-edge solutions but may lack the broader integration capabilities of larger vendors.
Traditional Security Vendors Going Quantum
Established security companies are adding quantum capabilities to existing portfolios:
- IBM: Quantum-safe cryptography integrated with broader security platforms
- Microsoft: Azure Quantum includes security components
- Google: Post-quantum experiments in Chrome browser
- Amazon: AWS implementing quantum-resistant encryption options
These vendors offer the advantage of integration with existing infrastructure but may not have the specialized expertise of pure-play companies.
Open Source Quantum Security Projects
The open-source community plays a crucial role in quantum security. Projects like those detailed in Cloudflare’s post-quantum blog provide transparency and community support:
Table 4: Key Open Source Quantum Security Resources
| Project | Description | Primary Use Case | Maturity Level |
|---|---|---|---|
| Open Quantum Safe (OQS) | Quantum-resistant algorithm library | General PQC implementation | Production-ready |
| liboqs | C library for post-quantum crypto | Low-level integration | Stable |
| PQCrypto-VPN | Quantum-resistant VPN | Network security | Beta |
| CIRCL (Cloudflare) | Crypto library with PQC | Web applications | Production |
| Qiskit | IBM’s quantum software | Algorithm development | Mature |
Open source options provide transparency and community support but require more internal expertise to implement effectively.
Quantum Security Myths and Realities
Separating quantum fact from fiction helps organizations make informed decisions. Let’s debunk some common myths about quantum threats and security.
Myth 1: Quantum Computers Will Break Everything Overnight
Reality: The quantum threat will likely emerge gradually. Early quantum computers will probably target specific types of encryption first, giving organizations time to respond. However, “harvest now, decrypt later” attacks mean the threat is already active in some sense.
Myth 2: Quantum Security Is Only for Government and Big Tech
Reality: Every organization handling sensitive data faces quantum threats. Small businesses might actually be more vulnerable because they often lack the resources for comprehensive security upgrades. The democratization of quantum computing means threats won’t discriminate by organization size.
Myth 3: Current Quantum Computers Can Already Break Encryption
Reality: Today’s quantum computers are still too small and error-prone to break real-world encryption. However, the pace of improvement is accelerating. Organizations shouldn’t panic but also shouldn’t be complacent.
Myth 4: Post-Quantum Cryptography Is Unproven
Reality: While newer than classical methods, post-quantum algorithms have undergone rigorous analysis. NIST’s standardization process involved years of cryptanalysis by the world’s best cryptographers. These algorithms are ready for deployment.
Myth 5: Quantum Security Is Too Expensive for Most Organizations
Reality: Costs are dropping rapidly as quantum security becomes mainstream. Cloud providers already offer quantum-safe options at minimal extra cost. The real expense comes from delayed action, not early adoption.
Future-Proofing Your Quantum Security Strategy
Building a quantum security strategy that stands the test of time requires thinking beyond current threats. Here’s how to create a future-proof approach that adapts as the quantum landscape evolves.
Continuous Learning and Adaptation
The quantum field moves incredibly fast. Organizations need mechanisms for staying current:
- Quantum threat intelligence: Subscribe to feeds tracking quantum computing progress
- Regular strategy reviews: Reassess quantum risks and defenses quarterly
- Academic partnerships: Connect with universities researching quantum security
- Industry collaboration: Share quantum security insights with peers
Static security strategies fail against dynamic threats. Build adaptation into your quantum security DNA.
Scenario Planning for Quantum Futures
Different quantum futures require different responses. Smart organizations plan for multiple scenarios:
- Slow quantum progress: Quantum threats emerge gradually over 15-20 years
- Quantum breakthrough: Sudden advancement makes current encryption obsolete
- Asymmetric quantum capabilities: Some nations/organizations get quantum computers first
- Quantum defense breakthrough: New defensive technologies neutralize quantum threats
Each scenario requires different preparations. Robust strategies work across multiple possible futures.
Building Quantum Security Culture
Technology alone won’t solve quantum threats. Organizations need cultural changes:
- Security awareness: Every employee understanding basic quantum risks
- Crypto-hygiene: Good practices around key management and algorithm selection
- Innovation mindset: Willingness to adopt new security approaches
- Risk acceptance: Understanding that perfect quantum security doesn’t exist
Cultural change takes time, making early starts crucial for quantum readiness.
The Competitive Advantage of Early Quantum Security
Organizations moving early on quantum security gain unexpected advantages beyond risk mitigation. Understanding these benefits helps justify quantum security investments.
Trust and Reputation Benefits
Customers increasingly care about data security. Organizations demonstrating quantum readiness build trust:
- Marketing differentiation: “Quantum-safe” becomes a selling point
- Partner preferences: Other quantum-ready organizations prefer similar partners
- Regulatory advantages: Early compliance with emerging quantum regulations
- Talent attraction: Security-conscious employees prefer quantum-ready employers
These soft benefits often exceed the hard ROI from risk reduction.
Innovation and Learning Spillovers
Quantum security projects drive broader innovation:
- Technical capabilities: Teams learn cutting-edge cryptography and system design
- Architectural improvements: Quantum preparation often reveals other security gaps
- Cultural transformation: Quantum projects build security-first mindsets
- Strategic thinking: Long-term quantum planning improves overall strategic capabilities
Organizations report that quantum security initiatives catalyze broader digital transformation efforts.
First-Mover Market Advantages
Early quantum security adoption creates market opportunities:
- New service offerings: Quantum security consulting for less-prepared competitors
- Intellectual property: Patents on quantum security implementations
- Ecosystem leadership: Shaping quantum security standards and practices
- Investment attraction: Quantum-ready companies attract forward-thinking investors
The quantum security market will explode as threats materialize. Early movers capture disproportionate value.
Conclusion: The Quantum Countdown Has Started
The quantum threat to current encryption isn’t science fiction it’s a mathematical certainty with an uncertain timeline. Organizations face a choice: prepare now while there’s time or scramble later when quantum computers mature. The “harvest now, decrypt later” threat means that in some sense, it’s already too late for data encrypted today with classical methods.
Smart organizations recognize that quantum security isn’t just about risk mitigation it’s about competitive advantage. Early movers build trust, develop capabilities, and position themselves as leaders in the quantum era. They understand that cyber security quantum challenges require action today, not tomorrow. For a comprehensive guide on implementing these defenses, visit our detailed post-quantum cryptography resource page.
The clock is ticking on current encryption methods. Every day of delay is another day of data vulnerable to future quantum attacks. The question isn’t whether to prepare for quantum threats but how quickly you can build quantum resilience.
Table 5: Quantum Security Readiness Checklist
| Action Item | Priority | Timeline | Resources Needed |
|---|---|---|---|
| Executive briefing on quantum risks | Critical | Week 1-2 | Security team, C-suite time |
| Cryptographic asset inventory | High | Month 1 | IT audit team |
| Vendor quantum roadmap assessment | High | Month 1-2 | Procurement, security |
| Pilot PQC implementation | Medium | Month 3-6 | Dev team, test environment |
| Budget allocation for quantum security | High | Month 2-3 | CFO, security leadership |
| Staff training on PQC | Medium | Month 3-4 | Training budget, time |
| Partner coordination | Medium | Month 4-6 | Business development |
| Full migration planning | Critical | Month 6+ | Cross-functional team |
As you’ve seen throughout this analysis, the quantum threat timeline affects every industry, every organization, and every piece of sensitive data. From financial services grappling with quantum cyber risk to healthcare providers protecting patient data for decades, the challenge is universal but the solutions must be tailored.
The good news? We’re still in the preparation window. Organizations acting now have time to implement thoughtful, cost-effective quantum defenses. The tools exist, the standards are emerging, and the path forward is clear for those willing to take it.
Your next step? Start the conversation in your organization. Share this analysis with your leadership team. Begin assessing your quantum vulnerabilities. Connect with quantum security experts. Most importantly, don’t wait for the quantum threat to materialize by then, it will be too late.
The quantum era is coming whether we’re ready or not. The only question is: will your organization be quantum-safe when it arrives? The countdown has started, and the time to act is now. Your future self and your future customers will thank you for starting the quantum security journey today.
Remember, in the race between quantum computers and quantum security, there’s no second place. There are only the prepared and the compromised. Which will you be when quantum threats become quantum reality?