Social Engineering Attacks: Psychology Behind Modern Cyber Threats

You know what keeps me up at night? It’s not the latest zero-day exploit or some sophisticated malware strain. It’s the fact that I’ve watched brilliant engineers, seasoned executives, and careful HR professionals all fall for social engineering attacks that, in hindsight, seemed obvious. After spending 15 years in cybersecurity, I’ve realized something crucial: we’re not dealing with a technology problem we’re dealing with a human one.
The uncomfortable truth is that social engineering attacks work because they exploit fundamental aspects of human psychology that we can’t simply patch or update. While companies pour millions into firewalls and intrusion detection systems, attackers are bypassing all of that by targeting the one vulnerability that never goes away: us.
Table of Contents
The Psychology Behind Why Social Engineering Attacks Work
Let me share something that happened just last month. A Fortune 500 CFO received a call from what he believed was his CEO, urgently requesting a wire transfer for a confidential acquisition. The voice sounded right, the timing aligned with ongoing negotiations, and the pressure was intense. Within 30 minutes, $1.2 million was gone. This wasn’t a failure of technology it was a masterclass in psychological manipulation tactics.
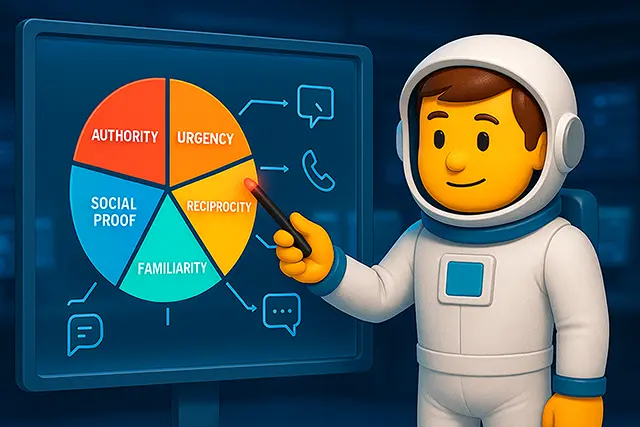
Social engineering techniques succeed because they exploit cognitive biases we all have. According to research from Stanford University’s Security Lab, these psychological vulnerabilities include:
Core Cognitive Biases Exploited by Attackers
| Cognitive Bias | How It’s Exploited | Defense Strategy |
|---|---|---|
| Authority Bias | Impersonating executives or IT staff | Establish verification protocols regardless of sender rank |
| Urgency Effect | Creating false deadlines and emergencies | Implement mandatory cooling-off periods for sensitive requests |
| Social Proof | “Everyone else has already complied” | Verify independently, never follow the crowd |
| Reciprocity | Offering help before asking for favors | Document all interactions with unknown parties |
| Familiarity Bias | Using insider knowledge and jargon | Trust but verify, even with “familiar” contacts |
Think about your own workday. How many decisions do you make under pressure? How often do you help colleagues without thoroughly verifying their identity? We’re wired to be helpful, to respect authority, and to act quickly when faced with urgency. Attackers know this, and they’re counting on it.
For a comprehensive overview of how these attacks fit into the broader threat landscape, see our complete guide to types of cyber attacks.
Common Social Engineering Techniques That Exploit Human Nature
The sophistication of modern social engineering attacks goes far beyond the Nigerian prince emails we used to mock. Today’s attackers are psychologists first, hackers second. They understand human psychology cyber attacks better than most security professionals understand firewalls.
The Evolution of Attack Techniques
1. Advanced Pretexting
- Weeks of target research and profiling
- Building detailed psychological profiles from social media
- Mimicking communication styles and company jargon
- Creating believable backstories with verifiable details
2. Sophisticated Baiting
- Personalized LinkedIn messages matching career goals
- Fake job opportunities at dream companies
- Investment opportunities aligned with financial interests
- Industry reports containing malware but valuable content
3. Weaponized Reciprocity
- Initial helpful actions (sending useful reports, solving problems)
- Building trust through multiple positive interactions
- Gradually escalating requests once trust is established
- Exploiting the psychological need to return favors
4. Multi-Stage Campaigns
- Phase 1: Information gathering through innocent interactions
- Phase 2: Trust building through helpful exchanges
- Phase 3: Compromise through targeted requests
- Phase 4: Lateral movement using gained credentials
The most insidious social engineering techniques exploit reciprocity our deep-seated need to return favors. An attacker might start by doing something helpful: sending you a useful industry report, helping you solve a technical problem, or connecting you with a valuable contact. Once they’ve triggered your reciprocity instinct, their later requests for “small favors” feel reasonable, even obligatory.
When these psychological attacks are combined with technical methods like phishing, the results can be devastating. Understanding both the human and technical elements is crucial for comprehensive protection.
The Remote Work Revolution’s Impact on Social Engineering Prevention
The shift to remote work hasn’t just changed where we work it’s fundamentally altered the landscape of social engineering attacks. The casual verification methods we relied on in offices (“Hey, did you just email me about that wire transfer?”) have vanished, replaced by digital communications that are far easier to spoof.
I’ve noticed a troubling pattern in the remote work era. Social engineering prevention has become harder because we’ve lost the subtle cues that helped us detect deception. You can’t see if someone’s desk is empty when they’re supposedly sending urgent requests. You can’t pick up on the nervous energy of a colleague who’s been compromised. We’re operating with less information while facing more sophisticated attacks.
Video call fatigue has created new vulnerabilities. After hours of Zoom meetings, we’re more likely to accept audio-only calls from “technical difficulties” or respond to chat messages without proper verification. Attackers have adapted their psychological manipulation tactics to exploit these new norms, often posing as IT support helping with the very collaboration tools we depend on.
The isolation of remote work also makes employees more vulnerable to social attacks. Without regular in-person interactions, we’re hungrier for connection and more likely to engage with friendly strangers online. Attackers exploit this loneliness, building relationships over weeks or months before making their move.

Building Effective Security Awareness Training That Actually Works
Here’s where most companies get security awareness training wrong: they treat it like a compliance checkbox rather than a fundamental shift in organizational culture. Showing employees a few PowerPoint slides about phishing once a year isn’t training it’s theater.
Components of Effective Security Training Programs
| Training Element | Traditional Approach | Effective Approach |
|---|---|---|
| Frequency | Annual compliance session | Continuous micro-learning |
| Format | Passive presentations | Interactive simulations |
| Content | Generic scenarios | Role-specific, relevant examples |
| Measurement | Completion rates | Behavior change metrics |
| Culture | Blame and shame | Learning and improvement |
| Follow-up | None | Regular reinforcement |
Effective training must acknowledge that social engineering techniques work because they exploit legitimate human needs and behaviors. Instead of telling employees to “be less trusting,” we need to give them practical tools for maintaining both security and productivity.
Key Elements of Successful Programs:
1. Experiential Learning
- Put employees in the attacker’s shoes
- Create safe spaces to fail and learn
- Use real-world simulations
- Gamify the learning experience
2. Clear Verification Protocols
- Simple, memorable procedures
- Multiple verification channels
- No exceptions for authority figures
- Quick reference guides at every desk
3. Cultural Integration
- Leadership buy-in and participation
- Celebration of security wins
- Blameless incident reviews
- Security as a shared responsibility
I’ve seen the most success with experiential learning that puts employees in the attacker’s shoes. When people understand human psychology cyber attacks from the attacker’s perspective, they develop an intuitive sense for manipulation that’s far more effective than memorizing rules.
The best social engineering prevention programs also address the organizational factors that make attacks successful. If your company culture punishes employees for missing deadlines but not for security lapses, you’re incentivizing risky behavior. According to the SANS Institute’s 2024 Security Awareness Report, organizations with mature security cultures see 70% fewer successful social engineering incidents.
Recognizing Manipulation Tactics Before You Become a Victim
After years of studying social engineering attacks, I’ve identified patterns in how our brains get hijacked. The most dangerous attacks don’t feel like attacks they feel like opportunities, emergencies, or routine requests that happen to come at vulnerable moments.
Red Flags Checklist for Social Engineering Attempts
- Urgency without precedent – Must be done in the next hour
- Secrecy requirements – Don’t tell anyone about this
- Authority pressure – The CEO personally requested this
- Emotional manipulation – Stories designed to trigger sympathy
- Bypassing procedures – Just this once, skip the normal process
- Too good to be true – Offers that seem unusually generous
- Odd communication channels – Boss emailing from personal account
- Grammar/style changes – Unusual writing patterns from known contacts
- Information fishing – Requesting data they should already have
- Technical difficulties – Can’t use video, phone isn’t working
Urgency is the universal red flag. When someone pushes you to act quickly, bypassing normal procedures because of an “emergency,” your defensive instincts should activate. Legitimate urgent requests can withstand a few minutes of verification. Psychological manipulation tactics often combine urgency with secrecy (“Don’t tell anyone about this acquisition”) to isolate victims from support systems that might spot the deception.
Common Emotional Triggers Used by Attackers
Fear-Based Tactics:
- Account suspension warnings
- Legal threat notifications
- Data breach alerts
- Job security threats
Greed-Based Tactics:
- Exclusive investment opportunities
- Lottery or inheritance notifications
- Special insider deals
- Performance bonuses
Sympathy-Based Tactics:
- Family emergency stories
- Charity requests
- Colleague in trouble abroad
- Medical crisis appeals
Watch for emotional manipulation that seems disproportionate to the situation. Social engineering techniques often involve dramatic stories designed to trigger empathy or fear. The sophistication of modern attacks means you might not recognize manipulation until it’s too late. That’s why building systematic defenses matters more than individual vigilance.
Sometimes these psychological attacks serve as the entry point for more technical compromises. When employees become insider threats through social engineering manipulation, the damage can be even more severe than external attacks.
The Role of Organizational Culture in Social Engineering Prevention
Company culture is either your strongest defense against social engineering attacks or your greatest vulnerability. I’ve consulted for organizations where security was so culturally embedded that attempted attacks were reported within minutes. I’ve also seen companies where fear of appearing foolish kept victims silent for days or weeks.
Human psychology cyber attacks succeed in environments where speed is valued over security, where questioning authority is discouraged, and where admitting mistakes carries severe consequences. If your employees are afraid to verify a CEO’s request or report a suspicious interaction, you’ve already lost the security battle.
Building a security-conscious culture starts with leadership. When executives openly discuss their own close calls with social engineering attacks, it normalizes vigilance and removes stigma. When managers praise employees for following verification procedures even when they slow down operations it reinforces that security matters.
The most resilient organizations treat security incidents as learning opportunities rather than failures. They conduct blameless post-mortems on social engineering techniques that succeeded, focusing on systemic improvements rather than individual punishment. This approach encourages reporting and creates a feedback loop that strengthens defenses over time.
Advanced Psychological Principles Used in Sophisticated Attacks
The cutting edge of social engineering attacks involves deep psychological profiling and multi-stage manipulation campaigns that would impress any therapist. Attackers aren’t just using Psychology 101 tricks anymore they’re applying advanced behavioral science to break down defenses systematically.
Modern attacks often begin with thorough reconnaissance that goes beyond technical details. Attackers analyze communication patterns, identify stress points, and map relationship dynamics within organizations. They know that targeting someone during their first week back from vacation, during quarter-end crunch time, or after a reorganization dramatically increases success rates.
Psychological manipulation tactics now include sophisticated priming techniques. Attackers might spend weeks sending legitimate-looking industry newsletters or helpful resources, training victims to click their links without suspicion. By the time the malicious payload arrives, the victim’s guard is completely down.
The principle of commitment and consistency our need to align actions with previous commitments gets weaponized in devastating ways. An attacker might start with tiny, harmless requests that gradually escalate. Each small compliance makes the next, larger request feel more reasonable. By the time victims realize they’re compromised, they’re too psychologically invested to back out.
Social engineering prevention must evolve to address these advanced techniques. This means understanding not just individual psychology but group dynamics, organizational psychology, and the specific vulnerabilities created by industry norms and corporate cultures.
Implementing Human-Centered Security Controls
Technology alone cannot solve human problems. The most effective defense against social engineering attacks acknowledges human nature and works with it rather than against it. This means designing security controls that enhance rather than hinder productivity.
Multi-channel verification should be seamless, not burdensome. When an employee receives an unusual request via email, they should have a clear, quick way to verify it through a different channel. This might mean secure messaging apps with verified contact lists, callback procedures using pre-established numbers, or verification codes that confirm identity without revealing sensitive information.
Security awareness training must be continuous and contextual. Instead of annual sessions, integrate micro-learning moments into daily work. When someone receives a wire transfer request, that’s when they need a quick reminder about verification procedures. When they’re added to a new project, that’s when they need guidance about information sharing boundaries.
The key to effective human psychology cyber attacks defense is reducing cognitive load. Security procedures should be simple enough to follow when stressed, clear enough to remember without constant reference, and flexible enough to accommodate legitimate urgent needs without creating dangerous exceptions.
Real Impact on American Businesses
The numbers are staggering, but they don’t tell the full story. Social engineering attacks cost American businesses over $4.2 billion last year, but the true damage extends far beyond financial losses. Trust erodes, careers end, and entire company cultures can shift toward paranoia and inefficiency.
Financial and Operational Impact by Business Size
| Business Size | Average Loss per Incident | Recovery Time | Most Common Attack Vector |
|---|---|---|---|
| Enterprise (1000+) | $1.8M | 3-6 months | Executive impersonation |
| Mid-Market (100-999) | $380K | 6-12 months | Vendor compromise |
| Small Business (<100) | $75K | 12+ months | Phishing/pretexting |
| Startups | $45K | Often fatal | Investment scams |
I’ve watched startups lose investor confidence not because of the money stolen, but because the breach revealed fundamental weaknesses in leadership and culture. I’ve seen decades-old business relationships destroyed when social engineering techniques were used to impersonate trusted partners.
Hidden Costs Beyond Financial Loss:
- Reputational damage lasting years after incident
- Employee turnover from breach of trust
- Increased operational friction from new security measures
- Legal fees and regulatory compliance costs
- Insurance premium increases
- Lost productivity during investigation and recovery
Small and medium businesses suffer disproportionately. While large corporations can absorb seven-figure losses and hire crisis management teams, a successful attack can literally end a smaller company. The democratization of psychological manipulation tactics means that sophisticated attacks once reserved for major targets now threaten businesses of every size.
The rise of business email compromise, powered by social engineering attacks, has made every employee a potential target and every email a potential threat. For deeper insights into the full spectrum of cyber threats facing businesses, explore our comprehensive guide to different types of cyber attacks.
Future-Proofing Against Evolving Social Engineering Tactics
As I look ahead, the convergence of artificial intelligence and social engineering attacks presents challenges we’re only beginning to understand. Deepfake audio and video will make verification exponentially harder. AI-powered chatbots can maintain dozens of personalized manipulation campaigns simultaneously. The psychological arms race is accelerating.
Emerging Threats on the Horizon
AI-Enhanced Attacks:
- Deepfake voice and video impersonation
- Automated psychological profiling
- Real-time conversation adaptation
- Mass personalization of attacks
New Attack Vectors:
- Virtual reality meeting infiltration
- IoT device social engineering
- Blockchain-based scams
- Quantum computing password attacks
Evolving Techniques:
- Long-term relationship building (months/years)
- Supply chain social engineering
- Hybrid attacks combining multiple vectors
- Nation-state psychological operations
Social engineering prevention must evolve from reactive training to proactive cultural transformation. Organizations need to build resilience into their DNA, creating systems and cultures that can withstand not just today’s attacks but whatever comes next.
Building Future-Ready Defenses:
- Zero-Trust Human Interactions
- Verify every request, regardless of source
- Multi-factor authentication for all sensitive actions
- Cryptographic verification for executive communications
- AI-Powered Defense Systems
- Behavioral analysis to detect anomalies
- Natural language processing to identify manipulation
- Automated alert systems for suspicious requests
- Continuous Adaptation
- Regular security culture assessments
- Rapid response to new attack patterns
- Cross-industry threat intelligence sharing
The future of security awareness training lies in personalization and adaptation. Just as attackers tailor their approaches to individual targets, defense training must adapt to individual learning styles, risk profiles, and role-specific vulnerabilities.
Frequently Asked Questions About Social Engineering Attacks
What exactly are social engineering attacks?
Social engineering attacks are psychological manipulation techniques used by cybercriminals to trick people into revealing confidential information, transferring money, or granting system access. Unlike technical hacking that exploits software vulnerabilities, these attacks exploit human psychology and trust. They’re particularly dangerous because they bypass even the most sophisticated security systems by targeting the human element.
How can I tell if I’m being targeted by social engineering?
Watch for these warning signs: unexpected urgency in requests, authority figures asking you to bypass normal procedures, requests for secrecy, emotional manipulation stories, or communications from unusual channels. If someone is pushing you to act quickly without time to think or verify, that’s a major red flag. Trust your instincts if something feels off about a request, it probably is.
What should I do if I think I’ve fallen for a social engineering attack?
Act immediately time is critical. First, report the incident to your IT security team or supervisor without delay. Change all potentially compromised passwords, especially for financial and email accounts. Document everything you remember about the attack while details are fresh. Don’t feel ashamed; even security experts fall for sophisticated social engineering techniques. The faster you report, the better chance of minimizing damage.
Why do smart people fall for these attacks?
Intelligence offers no immunity against psychological manipulation tactics. These attacks work because they exploit fundamental human traits like trust, helpfulness, and respect for authority qualities that make us effective employees and good people. Attackers often strike when targets are stressed, tired, or distracted, when our critical thinking is naturally diminished. It’s not about being smart or dumb; it’s about being human.
How often should companies conduct security awareness training?
Annual training is insufficient for effective social engineering prevention. Best practices include monthly micro-learning sessions, quarterly simulated attacks, and immediate training moments triggered by relevant events (like receiving wire transfer requests). The key is making security awareness part of daily work culture rather than a periodic checkbox exercise.
Can technology solutions prevent social engineering attacks?
While technology helps, it can’t fully prevent human psychology cyber attacks. Multi-factor authentication, email filters, and anomaly detection systems provide important layers of defense, but determined attackers can still manipulate people into bypassing these controls. The most effective defense combines technology with human awareness and strong organizational culture.
What’s the difference between phishing and social engineering?
Phishing is actually a subset of social engineering attacks. While all phishing involves social engineering (manipulating people through deceptive emails), social engineering encompasses a broader range of tactics including phone calls (vishing), text messages (smishing), in-person deception, and elaborate pretexting schemes. For detailed phishing-specific defenses, see our guide on how to prevent phishing attacks.
Are small businesses really at risk from sophisticated social engineering?
Absolutely. Small businesses are increasingly targeted because attackers know they often lack dedicated security staff and comprehensive security awareness training programs. The same social engineering techniques used against Fortune 500 companies are now being deployed against small businesses, often with devastating results since smaller companies have fewer resources to recover from successful attacks.
How can I build a security-conscious culture in my organization?
Start with leadership buy-in executives must model security-conscious behavior. Implement blameless incident reporting where employees are praised, not punished, for reporting suspicious activities. Make verification procedures simple and consistent. Celebrate security wins publicly. Most importantly, frame security as protecting the team and mission, not as compliance burden. When security becomes part of “how we do things here,” social engineering prevention becomes natural rather than forced.
What’s the future of social engineering attacks?
The convergence of AI and social engineering attacks will make future threats more personalized and harder to detect. Deepfake technology will enable perfect voice and video impersonation. AI will allow attackers to maintain hundreds of personalized manipulation campaigns simultaneously. However, AI will also power new defensive tools. The key is building organizational resilience and human awareness that can adapt to evolving threats.
Conclusion: The Human Side of Cybersecurity
After 15 years in this field, I’ve learned that the most sophisticated firewall can’t protect against a well-crafted lie, and the strongest encryption can’t secure a trusting heart. Social engineering attacks succeed because they target the very qualities that make us human: our desire to help, our respect for authority, our need for connection.
The path forward isn’t to become less human it’s to become more aware. Understanding the human psychology cyber attacks exploit helps us build defenses that work with human nature rather than against it. When we acknowledge our psychological vulnerabilities without shame, we can address them without fear.
Remember, falling for social engineering techniques doesn’t make you stupid it makes you human. The smartest people I know have been victims because intelligence isn’t immunity. What matters is creating systems, cultures, and habits that protect us when our psychology works against us.
As you return to your inbox after reading this, I challenge you to look at your recent communications differently. Which requests triggered urgency? Which leveraged authority? Which played on your emotions? Awareness is the first step in social engineering prevention, but it’s the systematic changes in culture, process, and technology that will ultimately protect us from the psychological predators in our digital world.
The battle against social engineering attacks isn’t won with better technology it’s won by better understanding ourselves.