Beyond Tomorrow’s Encryption: Essential Post-Quantum Tools That Will Shield Your Data from Quantum Attacks
Quantum computing isn’t science fiction anymore it’s getting real, fast. For decades, the idea lived mostly in academic papers and physics departments. But today, serious progress is being made, and that has big implications for how we protect digital information.
While these machines could revolutionize everything from healthcare to machine learning, there’s a flip side that keeps security professionals up at night: quantum computers may one day be able to crack the encryption that protects our most sensitive data. Think financial transactions, private communications, government secrets none of it was designed to hold up against this level of computational power.
That’s why the U.S. National Institute of Standards and Technology (NIST) has stepped in. After years of research and global collaboration, they’ve released a new set of encryption standards built specifically for a quantum future.
Table of Contents
The Quantum Threat Looming: Why Traditional Encryption Is Living on Borrowed Time
The urgency of this transition cannot be overstated. Martin Charbonneau, head of quantum safe networks at Nokia, suggests, “A good estimation of this timeline was constructed in the Global Risk Institute’s Quantum threat timeline report. In 2024, it estimated that by 2034, there was between a 17% and 34% chance that a cryptographically relevant quantum computer (CRQC) would exist capable of breaking RSA 2048 in 24 hours. The probability increases to 79% by 2044.”
| Timeframe | Probability of CRQC | Impact on Current Encryption | Recommended Action |
|---|---|---|---|
| 2025-2029 | < 10% | Current encryption remains secure | Begin inventory and planning |
| 2030-2034 | 17-34% | Growing risk to sensitive data | Implement hybrid cryptography |
| 2035-2039 | 50-65% | Critical threat to RSA/ECC | Complete migration for critical systems |
| 2040-2044 | 79%+ | Classical encryption compromised | Full post-quantum deployment required |
The quantum computing breakthrough timeline has accelerated dramatically in recent years. HQC was selected for standardization on March 11, 2025. Meanwhile, Microsoft has released early-access post-quantum cryptography (PQC) tools for Windows and Linux, allowing organizations to test quantum-resistant security ahead of emerging threats. These developments signal that the theoretical threat of quantum computing is rapidly becoming a practical reality that organizations must address immediately.
Perhaps the most insidious aspect of the quantum threat is the “harvest now, decrypt later” (HNDL) attack strategy. The fear is that adversaries will capture encrypted data today with plans to decrypt it in the future using quantum computers. This means that sensitive data encrypted with today’s standards medical records, financial information, government communications could already be compromised, waiting only for quantum computers powerful enough to break their encryption.
The mathematics behind this threat are well-established. Quantum computers leverage quantum mechanical phenomena like superposition and entanglement to solve certain mathematical problems exponentially faster than classical computers. Researchers around the world are racing to build quantum computers that would operate in radically different ways from ordinary computers and could break the current encryption that provides security and privacy for just about everything we do online.
Understanding Post-Quantum Cryptography: The Science Behind Quantum-Resistant Security
Post-quantum cryptography represents a fundamental shift in how we approach digital security. Unlike traditional encryption methods that rely on the computational difficulty of problems like integer factorization or discrete logarithms problems that quantum computers can solve efficiently post-quantum algorithms are built on mathematical problems that remain hard even for quantum computers.
The goal of post-quantum cryptography (also called quantum-resistant cryptography) is to develop cryptographic systems that are secure against both quantum and classical computers, and can interoperate with existing communications protocols and networks. This dual requirement security against both quantum and classical attacks while maintaining compatibility with existing infrastructure makes the development and implementation of post-quantum tools particularly challenging.
The quantum threat timeline varies depending on whom you ask, but most experts agree that organizations need to begin their migration now. Historically, it has taken almost two decades to deploy our modern public key cryptography infrastructure. Therefore, regardless of whether we can estimate the exact time of the arrival of the quantum computing era, we must begin now to prepare our information security systems to be able to resist quantum computing.
The NIST Standardization Process: A Milestone in Cryptographic History
The National Institute of Standards and Technology’s post-quantum cryptography standardization process represents one of the most significant collaborative efforts in the history of cryptography. In 2015, NIST initiated the selection and standardization of quantum-resistant algorithms to counter potential threats from quantum computers. After assessing 82 algorithms from 25 countries, the top 15 were identified with global cryptographers’ assistance.
The culmination of this massive undertaking came in 2024 when NIST released a final set of encryption tools designed to withstand the attack of a quantum computer. These post-quantum encryption standards secure a wide range of electronic information, from confidential email messages to e-commerce transactions that propel the modern economy.

Categories of Post-Quantum Tools: The New Cryptographic Arsenal
Lattice-Based Cryptographic Tools
Lattice-based cryptography has emerged as the cornerstone of post-quantum security. These algorithms derive their security from the difficulty of solving problems related to lattices in high-dimensional spaces problems that remain computationally intractable even for quantum computers.
| Algorithm Category | Example Algorithms | Key Advantages | Main Challenges | Best Use Cases |
|---|---|---|---|---|
| Lattice-Based | CRYSTALS-Kyber, CRYSTALS-Dilithium | Small key sizes, Fast performance | Relatively new mathematical foundation | General-purpose encryption, Digital signatures |
| Hash-Based | SPHINCS+, XMSS, LMS | Well-understood security, Quantum-proof | Large signature sizes | Long-term signatures, Code signing |
| Code-Based | Classic McEliece, HQC | Mature cryptanalysis, Strong security | Very large public keys | High-security applications |
| Multivariate | Rainbow, GeMSS | Fast signature verification | Large key sizes, Some variants broken | Embedded systems, IoT devices |
CRYSTALS-Kyber (ML-KEM)
CRYSTALS-Kyber, now standardized as ML-KEM (Module Lattice-Based Key Encapsulation Mechanism), represents the crown jewel of lattice-based key encapsulation mechanisms. FIPS 203, FIPS 204 and FIPS 205, which specify algorithms derived from CRYSTALS-Dilithium, CRYSTALS-KYBER and SPHINCS+, were published August 13, 2024.
Kyber offers three security levels Kyber512, Kyber768, and Kyber1024 providing flexibility for different security requirements. The algorithm’s efficiency and relatively small key sizes make it particularly attractive for real-world deployment. Major technology companies have already begun integrating Kyber into their systems, with Amazon now supports hybrid modes involving Kyber in their AWS Key Management Service and Cloudflare integrated Kyber alongside other PQ algorithms into CIRCL, the Cloudflare Interoperable, Reusable Cryptographic Library.
| Post-Quantum Tool | Public Key Size | Ciphertext/Signature Size | Speed (vs RSA-2048) | Security Level |
|---|---|---|---|---|
| Kyber-512 | 800 bytes | 768 bytes | 3x faster | Level 1 (AES-128) |
| Kyber-768 | 1,184 bytes | 1,088 bytes | 2.5x faster | Level 3 (AES-192) |
| Kyber-1024 | 1,568 bytes | 1,568 bytes | 2x faster | Level 5 (AES-256) |
| Dilithium-2 | 1,312 bytes | 2,420 bytes | 5x faster signing | Level 2 (AES-128) |
| Dilithium-3 | 1,952 bytes | 3,293 bytes | 4x faster signing | Level 3 (AES-192) |
| Dilithium-5 | 2,592 bytes | 4,595 bytes | 3x faster signing | Level 5 (AES-256) |
| SPHINCS+-128f | 32 bytes | 17,088 bytes | 100x slower | Level 1 (AES-128) |
CRYSTALS-Dilithium (ML-DSA)
For digital signatures, CRYSTALS-Dilithium (standardized as ML-DSA – Module Lattice-Based Digital Signature Algorithm) provides quantum-resistant authentication. Dilithium is a digital signature scheme that is strongly secure under chosen message attacks based on the hardness of lattice problems over module lattices.
The implementation of Dilithium requires careful attention to performance optimization. Recent research has shown significant improvements through vectorization, with AVX-512 implementation improves the performance by 43.2%/39.3%/45.6% in key generation, 36.6%/41.6%/43.7% in signing, and 45.3%/46.5%/47.4% in verification for the parameter sets of Dilithium2/3/5 respectively.
// Example: Digital signature using CRYSTALS-Dilithium
#include <oqs/oqs.h>
int sign_message_with_dilithium(const uint8_t *message,
size_t message_len) {
// Initialize Dilithium3 for post-quantum tools signing
OQS_SIG *sig = OQS_SIG_new(OQS_SIG_alg_dilithium_3);
// Allocate memory for keys and signature
uint8_t *public_key = malloc(sig->length_public_key);
uint8_t *secret_key = malloc(sig->length_secret_key);
uint8_t *signature = malloc(sig->length_signature);
size_t signature_len;
// Generate post-quantum signing keypair
OQS_SIG_keypair(sig, public_key, secret_key);
// Sign the message with post-quantum tools
OQS_SIG_sign(sig, signature, &signature_len,
message, message_len, secret_key);
// Verify the signature
OQS_STATUS verify_status = OQS_SIG_verify(sig, message,
message_len, signature,
signature_len, public_key);
if (verify_status == OQS_SUCCESS) {
printf("Signature verified successfully!\n");
}
// Cleanup
OQS_SIG_free(sig);
free(public_key);
free(secret_key);
free(signature);
Hash-Based Signature Tools
Hash-based signatures offer a unique advantage in the post-quantum landscape: their security relies solely on the properties of hash functions, making them arguably the most conservative choice for long-term security.
SPHINCS+ (SLH-DSA)
SPHINCS+, standardized as SLH-DSA (Stateless Hash-Based Digital Signature Algorithm), represents the pinnacle of hash-based signature schemes. An example of a hash-based post-quantum cryptographic algorithm is the Stateless Hash-Based Digital Signature Algorithm (SLH-DSA), formerly known as SPHINCS+.
Unlike other signature schemes that maintain state between signatures, SPHINCS+ is stateless, eliminating the risk of catastrophic security failures due to state reuse. This property makes it particularly suitable for applications where signature generation might occur across multiple devices or in distributed systems.
Code-Based Encryption Tools
Code-based cryptography, one of the oldest approaches to post-quantum security, derives its strength from the difficulty of decoding random linear codes.
Classic McEliece
Classic McEliece stands as a testament to the longevity of well-designed cryptographic systems. First proposed in 1978, it has withstood decades of cryptanalytic scrutiny. However, its main drawback remains its large public key size, which can reach several megabytes for high-security parameters.
HQC (Hamming Quasi-Cyclic)
HQC was selected for standardization on March 11, 2025. This recent addition to the NIST standards offers more practical key sizes compared to Classic McEliece while maintaining strong security guarantees.
Isogeny-Based and Multivariate Tools
While SIKE (Supersingular Isogeny Key Encapsulation) was broken during the NIST competition, research continues into other isogeny-based approaches. Multivariate polynomial cryptography, including schemes like Rainbow, continues to be explored for specific use cases despite some setbacks in the standardization process.
Practical Implementation Tools: Building Quantum-Safe Systems Today
Development Libraries
The transition to post-quantum cryptography requires robust, well-tested implementations. Several key libraries have emerged as essential tools for developers:
Open Quantum Safe (OQS)
liboqs is a C library for quantum-safe cryptographic algorithms, released under the MIT License. The Open Quantum Safe project provides comprehensive support for post-quantum algorithms, including:
// Example: Using liboqs with multiple post-quantum tools
#include <oqs/oqs.h>
#include <stdio.h>
void list_available_algorithms() {
printf("Available Post-Quantum Tools:\n");
printf("=============================\n");
// List KEM algorithms
printf("\nKey Encapsulation Mechanisms:\n");
for (int i = 0; i < OQS_KEM_algs_length(); i++) {
const char *alg_name = OQS_KEM_alg_identifier(i);
if (OQS_KEM_alg_is_enabled(alg_name)) {
printf(" - %s\n", alg_name);
}
}
// List signature algorithms
printf("\nDigital Signature Algorithms:\n");
for (int i = 0; i < OQS_SIG_algs_length(); i++) {
const char *alg_name = OQS_SIG_alg_identifier(i);
if (OQS_SIG_alg_is_enabled(alg_name)) {
printf(" - %s\n", alg_name);
}
}
}
- a collection of open-source implementations of quantum-safe key encapsulation mechanism (KEM) and digital signature algorithms
- Testing and benchmarking. liboqs includes a test harness and benchmarking routines to compare performance of post-quantum implementations in a common framework.
- Language wrappers. Post-quantum algorithms from liboqs can be used in a variety of other programming languages using the provided wrappers.
The library’s architecture makes it particularly suitable for integration into existing systems. liboqs is part of the Open Quantum Safe (OQS) project, which aims to develop and integrate into applications quantum-safe cryptography to facilitate deployment and testing in real world contexts.
PQClean
PQClean, in short, is an effort to collect clean implementations of the post-quantum schemes that are in the NIST post-quantum project. The project focuses on providing portable, readable implementations that can efficiently upstream into higher-level protocol integration efforts such as Open Quantum Safe; can easily be integrated into benchmarking frameworks such as SUPERCOP; can easily be integrated into frameworks targeting embedded platforms such as pqm4.
Testing and Validation Tools
The complexity of post-quantum algorithms necessitates comprehensive testing frameworks:
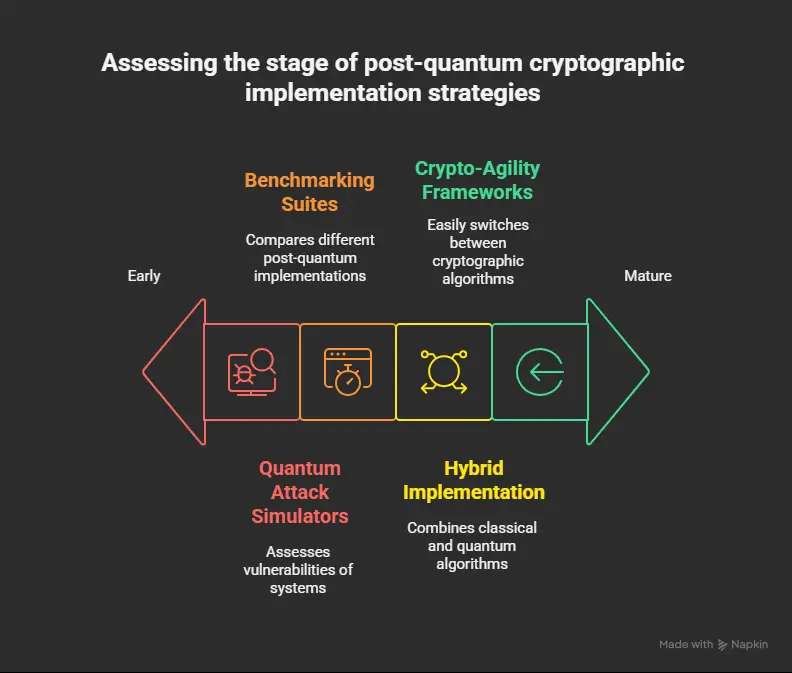
Benchmarking Suites
Performance evaluation is crucial for post-quantum deployment. Tools like SUPERCOP (System for Unified Performance Evaluation Related to Cryptographic Operations and Primitives) provide standardized benchmarking environments for comparing different implementations.
Quantum Attack Simulators
Understanding the quantum threat requires tools that can simulate quantum attacks. These simulators help researchers and security professionals assess the vulnerability of existing systems and validate the security of post-quantum implementations.
Migration and Integration Tools
The transition to post-quantum cryptography represents one of the most significant infrastructure challenges in the history of computing. Organizations need tools that can:
Crypto-Agility Frameworks
The underlying theme of Microsoft’s approach is what it calls “crypto agility” designing systems that can easily switch from one cryptographic algorithm to another as new threats emerge or standards change. This approach is essential because Microsoft emphasizes that PQC is still a developing field, and no one should assume today’s algorithms are the final answer.
Hybrid Implementation Solutions
The concept of hybrid cryptography using both classical and post-quantum algorithms simultaneously has emerged as a critical transitional strategy. Microsoft encourages a hybrid implementation combining classical and quantum-safe encryption methods, citing potential performance trade-offs, compatibility concerns, and the need for crypto-agile systems as PQC standards evolve.
Industry-Specific Post-Quantum Solutions: Tailored Security for Critical Sectors
Financial Sector Tools
The financial industry faces unique challenges in post-quantum migration. The 2024 Quantum Threat Timeline Report suggests that the timeline for the development of quantum computers that could threaten cryptography used for cybersecurity has accelerated. Financial institutions must protect:
| Financial System Component | Current Protection | Recommended Post-Quantum Tool | Migration Priority |
|---|---|---|---|
| Payment Card Processing | RSA-2048/AES-256 | Kyber-768 + AES-256 | Critical |
| SWIFT Messaging | RSA-4096 | Dilithium-3 + Kyber-1024 | Critical |
| Mobile Banking Apps | ECC-P256 | Kyber-512 (hybrid mode) | High |
| ATM Networks | 3DES/RSA | Kyber-768 + ChaCha20 | High |
| Cryptocurrency Wallets | ECDSA | Dilithium-2 + SPHINCS+ | Medium |
| Archive Encryption | AES-256 | Classic McEliece + AES-256 | Medium |
- Long-lived transaction records
- Customer authentication systems
- Inter-bank communication networks
- Cryptocurrency and blockchain systems
The implementation of quantum-safe VPN solutions is becoming critical for financial institutions that need to protect sensitive communications across their global networks.
Healthcare Encryption Upgrades
Healthcare organizations face particular urgency given the long-term sensitivity of medical records. Post-quantum tools for healthcare must address:
- Electronic Health Record (EHR) encryption
- Medical device security
- Telemedicine communications
- Research data protection
Government Communication Systems
Critical infrastructure systems rely on digital communications to transmit data. To secure the data in transit, cryptographic technologies are used to authenticate the source and protect the confidentiality and integrity of communicated and stored information.
Government agencies are leading the charge in post-quantum adoption. CISA’s Post-Quantum Cryptography (PQC) Initiative will unify and drive efforts with interagency and industry partners to address threats posed by quantum computing and to support critical infrastructure and government network owners and operators during the transition to post-quantum cryptography.
IoT Device Security
The Internet of Things presents unique challenges for post-quantum security:
- Resource-constrained devices
- Long deployment lifecycles
- Diverse communication protocols
- Massive scale of deployment
Hands-On Implementation Guide: From Theory to Practice
Setting Up Your First Post-Quantum Environment
Getting started with post-quantum cryptography requires a systematic approach. Here’s a practical guide to implementing your first quantum-safe system:
- Environment Preparation Begin by installing the necessary development tools. For most implementations, you’ll need:
- A C/C++ compiler (GCC, Clang, or MSVC)
- CMake for build management
- Python for testing scripts
- Git for version control
- Library Installation To download and build the software, follow the following steps:
# Clone the Open Quantum Safe library
$ git clone https://github.com/open-quantum-safe/liboqs.git
$ cd liboqs && mkdir build && cd build
# Configure and build the library
$ cmake -GNinja ..
$ ninja
# Install the library (optional)
$ sudo ninja install
- Basic Key Exchange Implementation Here’s a simple example using CRYSTALS-Kyber for key encapsulation:
#include <oqs/oqs.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int main() {
// Initialize Kyber-768 for post-quantum key exchange
OQS_KEM *kem = OQS_KEM_new(OQS_KEM_alg_kyber_768);
if (kem == NULL) {
printf("Failed to initialize Kyber-768\n");
return 1;
}
// Allocate memory for post-quantum tools components
uint8_t *public_key = malloc(kem->length_public_key);
uint8_t *secret_key = malloc(kem->length_secret_key);
uint8_t *ciphertext = malloc(kem->length_ciphertext);
uint8_t *shared_secret_e = malloc(kem->length_shared_secret);
uint8_t *shared_secret_d = malloc(kem->length_shared_secret);
// Generate quantum-resistant keypair
OQS_KEM_keypair(kem, public_key, secret_key);
// Encapsulation (sender side)
OQS_KEM_encaps(kem, ciphertext, shared_secret_e, public_key);
// Decapsulation (receiver side)
OQS_KEM_decaps(kem, shared_secret_d, ciphertext, secret_key);
// Verify shared secrets match
if (memcmp(shared_secret_e, shared_secret_d, kem->length_shared_secret) == 0) {
printf("Post-quantum key exchange successful!\n");
}
// Cleanup post-quantum tools resources
OQS_KEM_free(kem);
free(public_key);
free(secret_key);
free(ciphertext);
free(shared_secret_e);
free(shared_secret_d);
return 0;
}
Common Implementation Pitfalls and Solutions
- Performance Considerations Post-quantum algorithms typically require more computational resources than their classical counterparts. ML-KEM parameter sets include 512, 768 and 1024-bit options, which offer varying levels of security and come with trade-offs in performance
- Memory Management Many post-quantum algorithms use larger key sizes and require careful memory management. Always validate memory allocations and implement proper cleanup procedures.
- Side-Channel Resistance Implementing cryptographic algorithms requires attention to side-channel attacks. Use constant-time implementations where available and avoid branching on secret data.
- Integration with Existing Systems When integrating post-quantum tools with existing infrastructure, consider using hybrid modes that combine classical and post-quantum algorithms. This approach provides defense-in-depth and ensures compatibility during the transition period.
// Example: Hybrid key exchange combining ECDH and Kyber
#include <openssl/evp.h>
#include <oqs/oqs.h>
typedef struct {
uint8_t classical_key[32]; // ECDH shared secret
uint8_t pq_key[32]; // Post-quantum shared secret
uint8_t hybrid_key[32]; // Combined key material
} HybridKeyMaterial;
void derive_hybrid_key(HybridKeyMaterial *keys) {
// Combine classical and post-quantum tools keys using KDF
EVP_MD_CTX *mdctx = EVP_MD_CTX_new();
EVP_DigestInit_ex(mdctx, EVP_sha256(), NULL);
// Input both key materials
EVP_DigestUpdate(mdctx, keys->classical_key, 32);
EVP_DigestUpdate(mdctx, keys->pq_key, 32);
// Generate hybrid key for post-quantum security
EVP_DigestFinal_ex(mdctx, keys->hybrid_key, NULL);
EVP_MD_CTX_free(mdctx);
}
Testing and Validation
Comprehensive testing is essential for post-quantum implementations:
- Known Answer Tests (KATs) This implementation currently passes all KAT tests for kyber and ml_kem For more information, see the unit tests in test_kyber.py and test_ml_kem.py.
- Interoperability Testing Ensure your implementation can communicate with other post-quantum implementations. Test against reference implementations and widely-used libraries.
- Performance Benchmarking Monitor the performance impact of post-quantum algorithms on your systems. Use profiling tools to identify bottlenecks and optimize critical paths.
Integration with Modern Security Infrastructure
The adoption of post-quantum cryptography doesn’t happen in isolation. Organizations must consider how these new tools integrate with their existing security infrastructure, including zero trust security software and SaaS onboarding platforms.
Zero Trust Architecture and Post-Quantum Security
Zero trust security models assume no implicit trust and verify every transaction. Post-quantum cryptography enhances zero trust architectures by:
- Providing quantum-resistant authentication mechanisms
- Securing micro-segmentation boundaries
- Protecting identity and access management systems
- Ensuring long-term confidentiality of audit logs
Cloud Migration Considerations
As organizations migrate to cloud environments, post-quantum security becomes even more critical:
- Cloud providers are beginning to offer post-quantum options
- Hybrid cloud deployments require consistent security across environments
- Data residency and sovereignty concerns amplify the need for strong encryption
Future Roadmap and Strategic Recommendations
Timeline for Adoption
The path to full post-quantum adoption follows several phases:
2025-2026: Early Adoption Phase Governments and corporations will increase their focus on funding for quantum-resistant security upgrades in 2025. During this period:
- Critical infrastructure begins migration
- Major technology vendors release PQC-enabled products
- Standards bodies finalize implementation guidelines
2027-2030: Mainstream Integration
- Enterprise-wide deployments become common
- Legacy system migration accelerates
- Regulatory requirements emerge for critical sectors
2031-2035: Maturity Phase
- Post-quantum becomes the default for new systems
- Advanced quantum computers may emerge
- Second-generation post-quantum algorithms developed
Cost-Benefit Analysis
Organizations must carefully weigh the costs and benefits of post-quantum migration:
| Factor | Costs | Benefits | ROI Timeline |
|---|---|---|---|
| Implementation | $50K-$500K initial investment | Protection against quantum attacks | 5-10 years |
| Performance | 10-50% overhead for current algorithms | Future-proof security | Immediate |
| Training | $10K-$50K per team | Enhanced security expertise | 2-3 years |
| Infrastructure | 20-30% upgrade costs | Modernized systems | 3-5 years |
| Compliance | Audit and certification fees | Regulatory compliance | 1-2 years |
Strategic Planning for Organizations
Successful post-quantum migration requires comprehensive planning:
- Inventory and Assessment 64% of security leaders admit they “dread the day” the board asks about quantum migration plans, and 67% see the shift to post-quantum cryptography as a daunting task, given the lack of visibility into their certificates and keys. Organizations must:
- Catalog all cryptographic assets
- Assess data sensitivity and retention requirements
- Identify systems requiring immediate protection
- Phased Migration Approach
- Start with pilot projects in non-critical systems
- Implement hybrid cryptography for transition period
- Gradually expand to mission-critical applications
- Skills Development As PQC technologies mature, demand for cryptographers skilled in quantum-resistant protocols will surge. Universities and training programs will pivot to meet this need, offering specialized courses in post-quantum cryptography, quantum computing fundamentals, and secure software engineering.
- Vendor Management
- Assess vendor readiness for post-quantum transition
- Require PQC support in new procurement
- Plan for legacy system replacement or upgrade
The Road Ahead: Embracing Quantum-Safe Security
The transition to post-quantum cryptography represents both a challenge and an opportunity. John Preskill has some good observations on the evolving qubit zoo in his Q2B talk. Scaling remains a challenge for all gate-based systems, regardless of qubit type. While quantum computers capable of breaking current encryption may still be years away, the time to act is now.
Organizations that begin their post-quantum journey today will be better positioned to:
- Protect sensitive data against future threats
- Comply with emerging regulatory requirements
- Maintain customer trust and confidence
- Lead their industries in security innovation
The tools and technologies described in this article provide a comprehensive foundation for building quantum-safe systems. From the standardized algorithms like CRYSTALS-Kyber and CRYSTALS-Dilithium to the implementation libraries like Open Quantum Safe and PQClean, the ecosystem for post-quantum security is rapidly maturing.
As we stand at this cryptographic crossroads, the choice is clear: embrace post-quantum tools now, or risk leaving your data vulnerable to tomorrow’s quantum attacks. The quantum revolution is coming the question is not if, but when. By implementing post-quantum tools today, organizations can ensure their data remains secure not just for the present, but for the quantum future that lies ahead.
The journey to quantum-safe security may be complex, but with the right tools, planning, and commitment, organizations can successfully navigate this transition. The post-quantum era is not just about defending against future threats it’s about building a more secure, resilient digital infrastructure for generations to come.