Quantum Safe VPN: The Essential Guide to Post-Quantum Encryption for Future-Proof Security

The cryptographic landscape stands at a critical juncture. While quantum computers promise revolutionary advances in science and technology, they simultaneously threaten to unravel the encryption methods that protect our digital communications. This emerging reality has sparked an urgent need for quantum safe VPN a new generation of virtual private networks designed to withstand the computational power of quantum computers.
Organizations worldwide face an invisible threat that grows more serious each day. Sophisticated adversaries are already collecting encrypted data through “harvest now, decrypt later” attacks, betting on future quantum computers to break today’s encryption. This strategic data collection means that sensitive information transmitted today could become readable in the future, making the transition to quantum-resistant encryption not just prudent but essential.
Table of Contents
Understanding the Quantum Computing Threat to VPN Security
Traditional VPN encryption relies on mathematical problems that classical computers find extremely difficult to solve. RSA encryption, elliptic curve cryptography (ECC), and Diffie-Hellman key exchanges form the backbone of current VPN security. These algorithms derive their strength from the computational difficulty of factoring large prime numbers or solving discrete logarithm problems tasks that would take conventional computers thousands of years to complete.
Quantum computers operate on fundamentally different principles. Using quantum bits (qubits) that can exist in multiple states simultaneously through superposition, these machines can perform certain calculations exponentially faster than classical computers. Shor’s algorithm, developed in 1994, demonstrates how quantum computers could factor large integers and solve discrete logarithm problems in polynomial time, effectively breaking RSA, ECC, and other widely-used encryption methods.
The threat extends beyond theoretical mathematics. Current estimates suggest that a cryptographically relevant quantum computer (CRQC) capable of breaking today’s encryption could emerge as early as 2030, with some experts predicting this milestone might arrive by 2035. This timeline creates urgency for organizations handling sensitive data with long-term value.
What Makes a VPN Quantum-Safe?
A quantum safe VPN incorporates post-quantum cryptography (PQC) algorithms designed to resist attacks from both classical and quantum computers. These advanced encryption methods rely on mathematical problems that remain computationally difficult even for quantum systems. Unlike traditional encryption that depends on factorization or discrete logarithm problems, quantum-resistant algorithms utilize different mathematical foundations.
Post-quantum cryptographic algorithms typically fall into several categories:
- Lattice-based cryptography: Uses the difficulty of finding short vectors in high-dimensional lattices
- Hash-based cryptography: Relies on the security of cryptographic hash functions
- Code-based cryptography: Based on error-correcting codes and the difficulty of decoding random linear codes
- Multivariate polynomial cryptography: Uses systems of multivariate polynomial equations over finite fields
- Isogeny-based cryptography: Leverages walks on supersingular isogeny graphs
The National Institute of Standards and Technology (NIST) has standardized several quantum-resistant algorithms after years of rigorous testing. CRYSTALS-Kyber (now ML-KEM) emerged as the primary algorithm for general encryption, while CRYSTALS-Dilithium, FALCON, and SPHINCS+ were selected for digital signatures. These algorithms form the foundation of quantum safe VPN implementations.
The Harvest Now, Decrypt Later Threat Explained
Perhaps the most insidious aspect of the quantum threat is the “harvest now, decrypt later” (HNDL) attack strategy. Nation-state actors and sophisticated cybercriminals are actively intercepting and storing encrypted communications today, anticipating future quantum computers that can decrypt this data. This approach transforms encrypted data into a ticking time bomb, waiting for the arrival of sufficiently powerful quantum computers.
HNDL attacks target data with long-term value, including:
- Government secrets and classified information
- Corporate intellectual property and trade secrets
- Personal financial records and healthcare data
- Research and development documentation
- Strategic business communications
- Legal documents and contracts
The challenge with HNDL attacks lies in their invisibility. Organizations cannot detect when their encrypted data has been harvested, and by the time quantum computers can decrypt it, the damage becomes irreversible. This reality underscores why waiting for quantum computers to become mainstream before implementing quantum-safe encryption is a dangerous strategy.
How Quantum Safe VPN Work: Technical Implementation
Quantum safe VPN implement post-quantum cryptography through various approaches, with hybrid encryption emerging as the preferred method during the transition period. This approach combines classical encryption algorithms with quantum-resistant ones, ensuring security against both current and future threats.
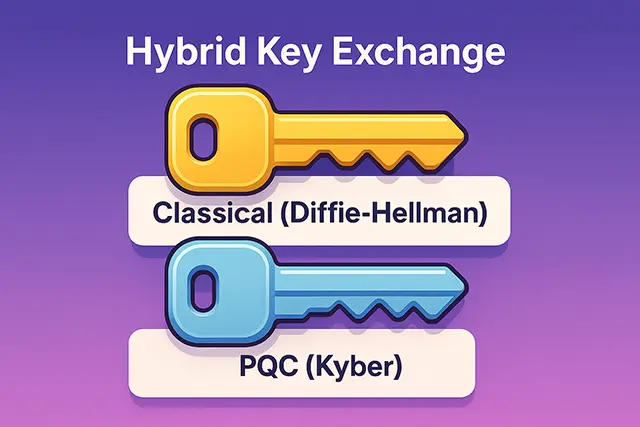
Hybrid Key Exchange Mechanisms
Modern quantum safe VPN utilize hybrid key exchange mechanisms that layer multiple encryption methods. For example, a connection might use traditional Diffie-Hellman combined with CRYSTALS-Kyber, creating a key that requires breaking both algorithms to compromise the connection. This belt-and-suspenders approach provides insurance against potential vulnerabilities in newer quantum-resistant algorithms.
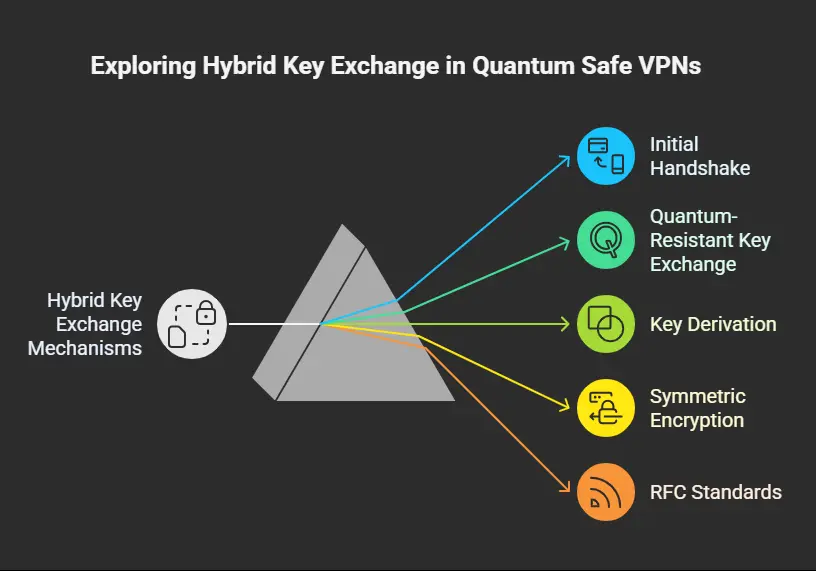
The implementation typically follows these steps:
- Initial handshake using classical encryption: Establishes backward compatibility
- Quantum-resistant key exchange: Adds post-quantum security layer
- Key derivation: Combines both keys using cryptographic functions
- Symmetric encryption: Uses the derived key for actual data transmission
Protocol Modifications and Standards
Several RFC standards guide quantum safe VPN implementations:
- RFC 8784: Provides a framework for mixing preshared keys in IKEv2 for post-quantum security
- RFC 9242: Enables intermediate key exchange in IKEv2 to handle larger PQC keys
- RFC 9370: Allows multiple key exchanges in IKEv2 for creating hybrid keys
These standards enable VPN protocols like IPsec and WireGuard to incorporate quantum-resistant algorithms without breaking existing infrastructure. The modifications allow for larger key sizes and multiple rounds of key exchange, accommodating the unique requirements of post-quantum cryptography.
Leading Quantum Safe VPN Solutions in 2025
Several VPN providers have emerged as leaders in implementing quantum-safe encryption, each taking different approaches to protect users against future quantum threats.
NordVPN: Pioneer in Consumer Quantum Protection
NordVPN has positioned itself at the forefront of consumer quantum safe VPN technology. Starting with a Linux implementation in September 2024, NordVPN expanded post-quantum encryption to all platforms by 2025. Their implementation uses the NordLynx protocol (based on WireGuard) enhanced with ML-KEM (Kyber) algorithm for quantum resistance.
Key features of NordVPN’s quantum-safe implementation include:
- Toggle-based activation: Users can enable quantum protection on-demand
- Platform-wide support: Available on Windows, macOS, iOS, Android, and TV platforms
- Minimal performance impact: Optimized to maintain connection speeds
- NIST-compliant algorithms: Uses standardized post-quantum cryptography
Palo Alto Networks: Enterprise-Grade Quantum Security
Palo Alto Networks offers comprehensive quantum safe VPN solutions for enterprise environments. Their PAN-OS implementation supports multiple quantum-resistant algorithms and allows organizations to configure up to eight rounds of key exchange, creating highly secure hybrid keys.
Enterprise features include:
- Multiple PQC algorithm support: ML-KEM, HQC, BIKE, and others
- Backward compatibility: Automatic fallback to classical encryption
- Granular configuration: Administrators can customize security profiles
- Crypto-agility: Easy algorithm switching as standards evolve
Microsoft’s Post-Quantum Cryptography VPN
Microsoft Research has developed an experimental fork of OpenVPN incorporating post-quantum cryptography. While primarily a research project, it demonstrates practical implementation approaches and provides valuable insights for the industry. The project emphasizes testing and evaluation of quantum-resistant algorithms in real-world VPN scenarios.
QAL VPN: Dedicated Quantum-Safe Solution
QAL VPN represents one of the first consumer VPNs built from the ground up with quantum resistance in mind. It implements NIST-selected algorithms and focuses on providing seamless quantum-safe connections without requiring technical expertise from users.
Implementation Challenges and Solutions
Transitioning to quantum safe VPN presents several technical and operational challenges that organizations must navigate carefully.
Performance Considerations
Post-quantum algorithms typically require larger key sizes and more computational resources than classical encryption. CRYSTALS-Kyber keys can be 10-50 times larger than equivalent RSA keys, potentially impacting connection establishment times and bandwidth usage. However, modern implementations have minimized these impacts through optimization techniques:
- Hardware acceleration: Leveraging dedicated cryptographic processors
- Algorithm optimization: Improving implementation efficiency
- Selective application: Using PQC only for key exchange, not bulk encryption
- Caching mechanisms: Reducing repeated computations
Compatibility and Interoperability
Legacy systems often cannot support quantum-safe algorithms without significant modifications. Organizations face challenges including:
- Protocol limitations: Older VPN protocols may not handle larger key sizes
- Device constraints: Embedded systems with limited resources
- Third-party integration: Ensuring compatibility with partner systems
- Certificate infrastructure: Updating PKI to support new algorithms
The solution involves implementing hybrid approaches that maintain backward compatibility while adding quantum resistance. This allows gradual migration without disrupting existing operations.
Standardization and Algorithm Selection
With multiple quantum-resistant algorithms available, organizations must carefully select appropriate options. Considerations include:
- NIST recommendations: Following standardized algorithms reduces risk
- Algorithm diversity: Using multiple algorithms provides redundancy
- Performance requirements: Balancing security with operational needs
- Future flexibility: Maintaining crypto-agility for algorithm updates
The Business Case for Quantum Safe VPN
Organizations evaluating quantum safe VPN adoption must consider both immediate benefits and long-term risk mitigation. The quantum threat timeline suggests that proactive adoption provides significant advantages.
Immediate Benefits
- Protection against HNDL attacks: Securing data harvested today
- Regulatory compliance: Meeting emerging quantum-readiness requirements
- Competitive advantage: Demonstrating security leadership
- Customer trust: Assuring stakeholders of data protection
Long-term Risk Mitigation
- Data longevity protection: Securing information valuable decades from now
- Transition readiness: Avoiding rushed implementations when quantum threats materialize
- Infrastructure modernization: Using quantum readiness to drive security improvements
- Supply chain security: Protecting communications with partners and vendors
Cost Considerations
While implementing quantum safe VPN requires investment, the costs pale compared to potential breaches of long-term sensitive data. Organizations should consider:
- Implementation costs: Software upgrades, hardware requirements, training
- Operational impact: Performance testing, compatibility verification
- Risk mitigation value: Preventing future data compromise
- Competitive positioning: Market differentiation through advanced security
Best Practices for Quantum Safe VPN Deployment
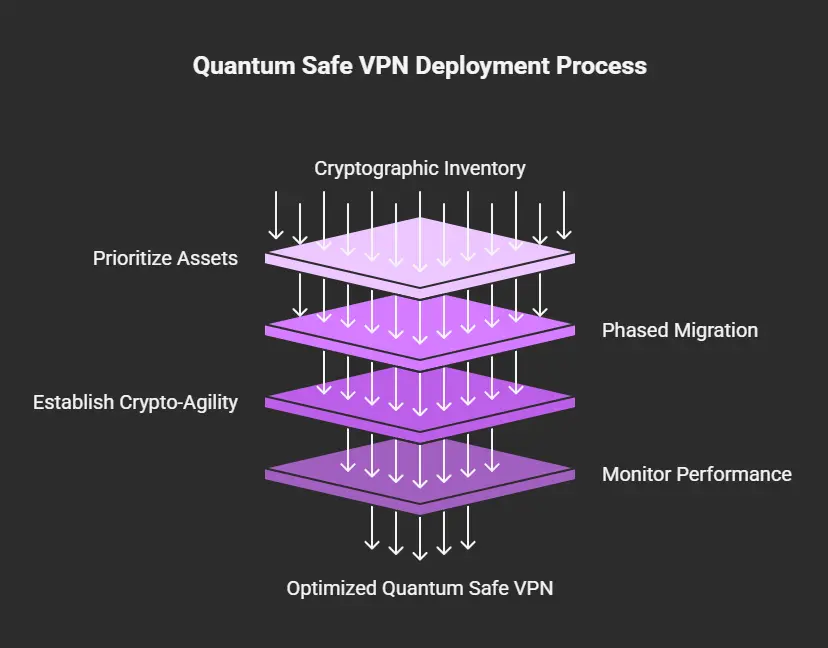
Successful quantum safe VPN implementation requires careful planning and systematic execution. Organizations should follow these best practices:
1. Conduct Cryptographic Inventory
Begin by cataloging all cryptographic implementations across your infrastructure:
- Identify all VPN endpoints and their current encryption methods
- Document certificate authorities and key management systems
- Map data flows and encryption dependencies
- Assess third-party cryptographic integrations
2. Prioritize High-Value Assets
Focus initial quantum-safe deployments on protecting:
- Long-term sensitive data (10+ year relevance)
- Intellectual property and trade secrets
- Strategic communications and planning documents
- Customer data with extended retention requirements
3. Implement Phased Migration
Adopt a gradual approach to minimize disruption:
- Phase 1: Deploy quantum safe VPN for critical connections
- Phase 2: Extend to high-value data transfers
- Phase 3: Migrate remaining connections
- Phase 4: Decommission legacy encryption
4. Establish Crypto-Agility
Build flexibility into your quantum-safe implementation:
- Use modular architectures supporting algorithm updates
- Implement centralized cryptographic policy management
- Maintain multiple algorithm options
- Plan for rapid algorithm replacement if vulnerabilities emerge
5. Monitor and Optimize Performance
Continuously assess the impact of quantum-safe encryption:
- Establish performance baselines before migration
- Monitor connection times and throughput
- Optimize configurations based on real-world usage
- Balance security requirements with operational needs
Quantum Key Distribution vs. Post-Quantum Cryptography
While post-quantum cryptography represents the primary approach for quantum safe VPN, quantum key distribution (QKD) offers an alternative method leveraging quantum mechanics principles.
Understanding QKD
QKD uses quantum properties to detect eavesdropping during key exchange. Any attempt to intercept quantum-encoded keys disturbs their quantum state, alerting communicating parties to the intrusion. This provides theoretical perfect security based on physics rather than computational difficulty.
QKD Limitations
Despite its theoretical advantages, QKD faces practical limitations:
- Distance constraints: Limited to ~100km without quantum repeaters
- Infrastructure requirements: Needs dedicated fiber optic connections
- Cost considerations: Expensive specialized hardware
- Scalability challenges: Point-to-point connections only
PQC Advantages
Post-quantum cryptography offers more practical benefits for VPN implementations:
- Software-based: Works with existing infrastructure
- Distance-independent: No physical limitations
- Cost-effective: Minimal hardware requirements
- Scalable: Supports complex network topologies
For most organizations, PQC-based quantum safe VPN provide the optimal balance of security, practicality, and cost-effectiveness.
The Future of Quantum Safe VPN Technology
The evolution of quantum safe VPN will accelerate as quantum computing advances and standards mature. Several trends shape the future landscape:
Emerging Technologies
- Homomorphic encryption integration: Enabling computation on encrypted data
- Zero-knowledge proofs: Enhanced privacy without revealing information
- Distributed quantum-safe networks: Mesh VPNs with quantum resistance
- AI-driven threat detection: Identifying potential HNDL attacks
Regulatory Evolution
Governments worldwide are developing quantum-readiness requirements:
- U.S. Quantum Computing Cybersecurity Preparedness Act: Mandating federal agency transitions
- EU quantum-safe initiatives: Protecting critical infrastructure
- Industry-specific regulations: Financial and healthcare quantum requirements
- International standards: Cross-border quantum-safe communications
Market Dynamics
The quantum safe VPN market will experience significant growth:
- Increased competition: More providers offering quantum-safe options
- Feature differentiation: Advanced quantum-resistant capabilities
- Price optimization: Quantum security becoming standard rather than premium
- Ecosystem development: Integration with broader security platforms
Industry-Specific Quantum Safe VPN Requirements
Different industries face unique challenges and requirements when implementing quantum safe VPN.
Financial Services
Banks and financial institutions handle transactions and records with decades-long relevance. Key requirements include:
- Transaction integrity: Protecting payment records from future tampering
- Regulatory compliance: Meeting quantum-readiness mandates
- High-performance needs: Maintaining transaction processing speeds
- Multi-party security: Protecting inter-bank communications
Healthcare
Medical records require protection for patient lifetimes and beyond. Healthcare organizations need:
- HIPAA compliance: Ensuring quantum-safe protection meets regulations
- Long-term confidentiality: Protecting records for 50+ years
- Research data security: Safeguarding clinical trial information
- Telemedicine protection: Securing remote consultations
Government and Defense
National security information demands the highest levels of quantum protection:
- Classified data protection: Preventing foreign intelligence decryption
- Critical infrastructure: Securing power grids and utilities
- Diplomatic communications: Protecting sensitive negotiations
- Emergency response networks: Ensuring crisis communication security
Technology and Research
Companies developing cutting-edge technologies face immediate HNDL threats:
- IP protection: Securing patents and trade secrets
- R&D communications: Protecting development discussions
- Supply chain security: Safeguarding vendor communications
- Competitive intelligence: Preventing corporate espionage
Measuring Quantum Safe VPN Effectiveness
Organizations must establish metrics to evaluate their quantum safe VPN implementations:
Security Metrics
- Algorithm strength: Bit security levels against quantum attacks
- Key exchange frequency: Minimizing exposure windows
- Hybrid implementation coverage: Percentage of connections using PQC
- Vulnerability assessment results: Regular security testing outcomes
Performance Metrics
- Connection establishment time: Impact of larger key sizes
- Throughput degradation: Bandwidth impact percentage
- CPU utilization: Processing overhead for PQC algorithms
- Latency increases: Additional delay from quantum-safe encryption
Operational Metrics
- Migration progress: Percentage of connections upgraded
- Compatibility issues: Number of integration problems
- User adoption rates: Activation of quantum-safe features
- Support ticket volume: Issues related to PQC implementation
Common Misconceptions About Quantum Safe VPN
Several misconceptions can hinder quantum safe VPN adoption. Understanding the reality helps organizations make informed decisions.
Misconception 1: “Quantum Computers Are Decades Away”
Reality: While large-scale quantum computers may be 5-10 years away, the HNDL threat exists today. Data encrypted now without quantum protection could be decrypted when quantum computers arrive, making immediate action necessary.
Misconception 2: “Quantum-Safe Means Completely Secure”
Reality: Quantum safe VPN protect against quantum computing threats but don’t eliminate all security risks. Organizations still need comprehensive security strategies addressing other attack vectors.
Misconception 3: “Only Governments Need Quantum Protection”
Reality: Any organization with long-term valuable data needs quantum protection. This includes businesses with intellectual property, customer records, or strategic plans.
Misconception 4: “Implementation Is Too Complex”
Reality: Modern quantum safe VPN solutions offer user-friendly implementations. Many providers offer simple toggle switches to enable quantum protection without technical expertise.
Misconception 5: “Performance Impact Is Prohibitive”
Reality: While early implementations showed significant performance impacts, current optimized solutions maintain acceptable speeds. Most users won’t notice the difference in daily usage.
Preparing Your Organization for Quantum-Safe Migration
Successful quantum safe VPN adoption requires organizational preparation beyond technical implementation.
Building Stakeholder Support
- Executive education: Help leadership understand quantum threats
- Risk assessment presentation: Quantify potential impact of HNDL attacks
- Competitive analysis: Show how competitors are addressing quantum threats
- ROI demonstration: Calculate long-term value of quantum protection
Developing Internal Expertise
- Training programs: Educate IT staff on post-quantum cryptography
- Certification pursuit: Encourage quantum security certifications
- Vendor partnerships: Leverage external expertise during transition
- Knowledge sharing: Create internal quantum security communities
Creating Migration Roadmaps
- Timeline development: Set realistic migration milestones
- Resource allocation: Budget for implementation and training
- Risk prioritization: Focus on highest-value targets first
- Contingency planning: Prepare for implementation challenges
Frequently Asked Questions About Quantum Safe VPN
What is the most trusted quantum safe VPN in the world?
NordVPN currently leads the consumer market with its comprehensive post-quantum encryption implementation across all platforms. For enterprise solutions, Palo Alto Networks and Fortinet offer highly trusted quantum safe VPN options. The “most trusted” designation depends on specific use cases consumers generally prefer NordVPN’s user-friendly approach, while enterprises often choose solutions from established security vendors with proven track records.
Is VPN safer than home WiFi against quantum threats?
A quantum safe VPN provides significantly better protection than home WiFi against quantum threats. While home WiFi encryption (WPA2/WPA3) protects local network traffic, it doesn’t secure data once it leaves your router. Quantum safe VPN encrypt your entire internet connection with post-quantum algorithms, protecting against HNDL attacks regardless of your network type.
Why is Google One getting rid of VPN?
Google discontinued its VPN service in Google One to focus on core storage features and reduce service complexity. This decision wasn’t related to quantum threats but rather strategic product positioning. Users seeking quantum-safe protection should consider dedicated VPN providers actively implementing post-quantum cryptography.
Is NordVPN safe for banking with quantum protection?
Yes, NordVPN with quantum-safe encryption enabled provides excellent protection for online banking. The post-quantum algorithms protect your financial data from both current threats and future quantum computers. However, always ensure you’re connecting to legitimate banking websites and enable all available security features on your accounts.
How much is NordVPN per month with quantum features?
NordVPN includes quantum-safe encryption at no additional cost in their standard plans, which start around $3.09-$12.99 per month depending on subscription length. The post-quantum protection is included as a free feature that users can enable, making it one of the most cost-effective quantum safe VPN options available.
Is there a downside to using quantum safe VPN?
The primary considerations include slightly larger data overhead due to bigger key sizes and potential compatibility issues with some legacy systems. However, modern implementations minimize these impacts. Most users experience negligible performance differences, and the security benefits far outweigh any minor drawbacks.
When should you not use VPN with quantum protection?
Quantum-safe features might be unnecessary for casual browsing of public information or when maximum speed is critical for non-sensitive activities. Some users may choose to disable quantum protection when streaming content or gaming, though the performance impact is usually minimal with optimized implementations.
Can WiFi networks block quantum safe VPN connections?
WiFi networks can potentially block any VPN traffic, including quantum-safe connections. However, quantum safe VPN use the same connection protocols as regular VPNs, making them no more likely to be blocked. Networks that allow standard VPN connections will typically support quantum-safe variants.
Which type of VPN is more secure against quantum attacks?
VPNs implementing hybrid post-quantum cryptography with multiple algorithms offer the highest security against quantum attacks. Look for solutions using NIST-standardized algorithms like ML-KEM (Kyber) combined with classical encryption. WireGuard-based implementations with PQC additions currently offer an optimal balance of security and performance.
What VPN protocols support quantum resistance?
IPsec with IKEv2 modifications (RFC 8784, 9242, 9370) and WireGuard with post-quantum extensions currently offer the best quantum resistance. OpenVPN can be modified for PQC support, though implementations vary. Proprietary protocols like NordLynx (WireGuard-based) have integrated quantum-safe features most seamlessly.
Does VPN track what you do with quantum encryption?
Quantum-safe encryption doesn’t change VPN logging policies. Reputable providers with no-logs policies don’t track user activity regardless of encryption type. Quantum protection only affects the encryption strength, not privacy policies. Always verify a provider’s logging policy independently of their quantum-safe features.
What is Quantum VPN on my phone?
Quantum VPN on phones refers to mobile VPN apps with post-quantum encryption capabilities. For example, NordVPN’s mobile apps allow users to enable quantum-safe protection through settings. This feature encrypts mobile data with quantum-resistant algorithms, protecting sensitive information accessed via smartphones.
How does quantum security work in practice?
Quantum security in VPNs works by using mathematical problems that remain difficult even for quantum computers. When you connect, the VPN performs a hybrid key exchange using both classical and quantum-resistant algorithms. This creates encryption keys that would require impractical amounts of time to break, even with quantum computing power.
Conclusion: The Quantum-Safe Imperative
The transition to quantum safe VPN represents more than a technical upgrade it’s a fundamental shift in how we approach long-term data security. As quantum computing advances from theoretical possibility to practical reality, organizations face a critical decision point. The invisible threat of harvest now, decrypt later attacks means that every day of delay potentially exposes more sensitive data to future decryption.
The good news is that quantum safe VPN technology has matured significantly. From NordVPN’s user-friendly consumer implementation to enterprise-grade solutions from Palo Alto Networks and others, organizations of all sizes can begin their quantum-safe journey today. The standardization of post-quantum algorithms by NIST provides a solid foundation for these implementations, while ongoing optimization efforts have minimized performance impacts.
Success in the quantum era requires action now, not when quantum computers become mainstream. Organizations must assess their cryptographic infrastructure, identify high-value data requiring long-term protection, and implement quantum safe VPN as part of a comprehensive security strategy. The investment in quantum safe technology today prevents potentially catastrophic data breaches tomorrow.
As we stand at the threshold of the quantum computing age, the question isn’t whether to implement quantum safe VPN, but how quickly organizations can adapt. Those who act decisively to protect their data with post-quantum cryptography will maintain their competitive advantage and stakeholder trust. Those who wait risk having their encrypted secrets become an open book when quantum computers arrive.
The path forward is clear: embrace quantum safe VPN technology, build crypto-agility into your infrastructure, and prepare for a future where computational power exceeds anything we’ve previously imagined. The quantum revolution is coming make sure your data is ready for it.